Ensuring Service and Action Restriction Across Multiple AWS Accounts
Question
Your company is planning to set up multiple accounts in AWS.
The IT Security department must ensure that certain services and actions are not allowed across all accounts.
How would you achieve this in the most effective way possible?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
The AWS Documentation mentions the following.
An AWS organization is an entity that you create to consolidate your AWS accounts.
A service control policy is a policy that specifies the services and actions that users and roles can use in the accounts that the SCP affects.
Option A is incorrect since you can't have a common IAM policy.
Option B is incorrect since this is an ineffective way of managing centralized control.
Option C is incorrect since AWS should not be responsible for denying the usage of services in an account.
For more information on AWS Organizations, please refer to the below URL-
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_getting-started_concepts.html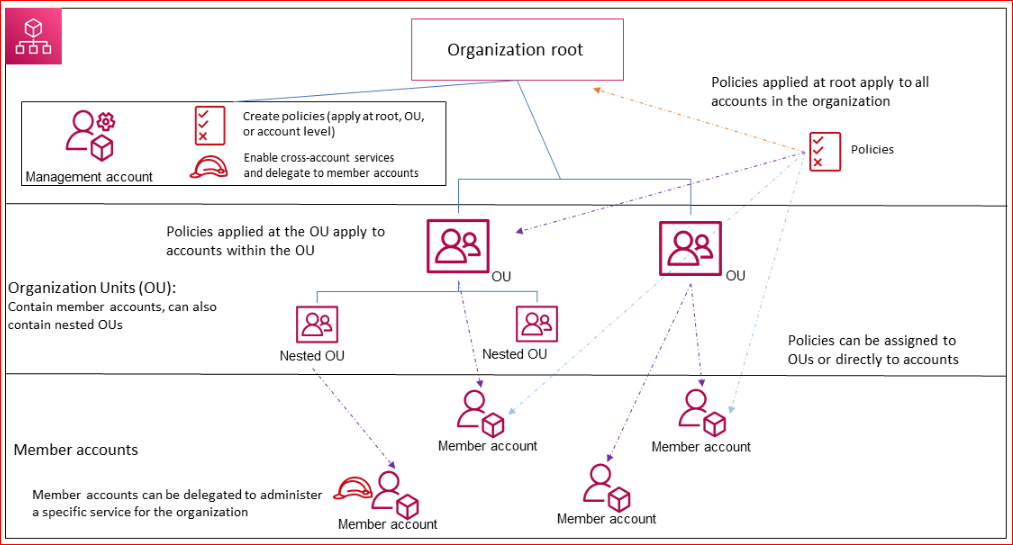
The most effective way to restrict certain services and actions across multiple AWS accounts is by using AWS Organizations and Service Control Policies (SCPs). Therefore, the correct answer is D.
AWS Organizations is a service that enables you to consolidate multiple AWS accounts into an organization that you create and centrally manage. AWS Organizations provides features like consolidated billing and access management for all accounts within an organization. You can use AWS Organizations to apply Service Control Policies (SCPs) to restrict permissions across all accounts in your organization.
Service Control Policies (SCPs) are a type of policy in AWS that you can use to control the services and actions that users and roles can access across multiple accounts in your organization. SCPs allow you to restrict permissions at the root level of your organization, at the organizational unit level, or at the account level. SCPs can be used to allow or deny access to AWS services and actions, and they override any permissions that are granted by IAM policies.
Creating a common IAM policy that can be applied across all accounts (Option A) may work, but it will require more maintenance effort and can lead to inconsistencies between accounts. Additionally, IAM policies only apply to a single account, so managing policies across multiple accounts is difficult.
Creating an IAM policy per account and applying them accordingly (Option B) may be appropriate for a small number of accounts, but it becomes impractical when managing large numbers of accounts. It can be difficult to keep track of multiple policies, and it can also lead to inconsistencies in permissions.
Denying the services to be used across accounts by contacting AWS (Option C) is not a practical solution, as it is time-consuming, and it may be impossible to get AWS to comply with such a request.
Therefore, the most effective way to restrict certain services and actions across multiple AWS accounts is by using AWS Organizations and Service Control Policies (Option D). It allows you to centrally manage the permissions and access across all accounts in your organization, providing a consistent and efficient approach to security management.
