AWS API Gateway Security Measures
Question
In AWS API Gateway, which of the following security measures is provided default by AWS to protect the backend systems?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: C.
API Gateway supports throttling settings for each method or route in your APIs.
You can set a standard rate limit and a burst rate limit per second for each method in your REST APIs and each route in WebSocket APIs.
Further, API Gateway automatically protects your backend systems from distributed denial-of-service (DDoS) attacks, whether attacked with counterfeit requests (Layer 7) or SYN floods (Layer 3).
Options A and B are part of the above list and do not have any default configurations.
Option C is correct.
Option D's statement is incorrect as it is a distractor.
The above screenshot shows AWS automatically protects from DDoS attacks.
Reference:
https://aws.amazon.com/api-gateway/faqs/ https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-control-access-to-api.html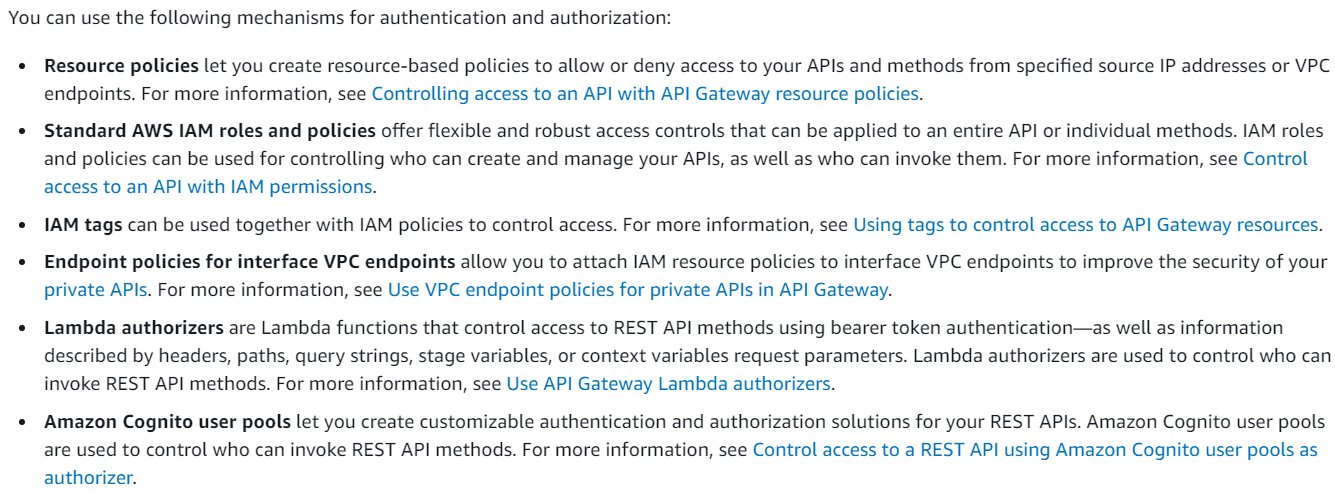
In AWS API Gateway, the security of backend systems is the responsibility of the customer. However, AWS provides different mechanisms to protect the backend systems, which are not configured by default. Therefore, option D is the correct answer.
Let's take a look at each of the options:
A. Default Cross-Origin Resource Sharing (CORS) configuration: CORS is a security mechanism used by web browsers to prevent web pages from making requests to a different domain. While API Gateway does provide support for CORS, it is not a default security measure to protect backend systems.
B. Default Resource Policy: Resource policies are used to define access control for AWS resources. While they are important for securing access to API Gateway, they are not a default security measure to protect backend systems.
C. Protection from distributed denial-of-service (DDoS) attacks: AWS provides protection against DDoS attacks through its AWS Shield service, which is enabled by default for all AWS customers. However, this protection is not specific to API Gateway and does not protect backend systems.
D. Security of backend systems falls under customer responsibility. AWS provides different mechanisms to protect backend systems which are not configured by default: This is the correct answer. While AWS provides a number of security mechanisms to help protect backend systems, it is ultimately the responsibility of the customer to properly configure and secure their own systems.
In conclusion, while AWS provides many security measures to protect API Gateway, the security of backend systems is the customer's responsibility. AWS provides different mechanisms to protect backend systems, but these mechanisms are not configured by default.