Increase AssumeRoleWithWebIdentity DurationSeconds to Resolve API Error
Question
Your company uses a web identity federation to manage user identities.
Some users call the AssumeRoleWithWebIdentity API to assume an IAM role to access the AWS RDS resources. The session duration is set as 1 hour.
Users complain that the timer is too short and increase the DurationSeconds to 2 hours in the AssumeRoleWithWebIdentity API.
However, the operation has failed. How would you resolve this problem?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: C.
Option A is incorrect because the maximum session duration is defined in the IAM role instead of the web identity provider.
Option B is incorrect because the session duration can be adjusted depending on the needs.
In this scenario, the operation has failed because the new value is larger than the maximum value allowed in the IAM role.
Resending the API for the credentials before the session expires would not help.
Option C is CORRECT because, by default, the temporary security credentials created by AssumeRoleWithWebIdentity last for one hour.
However, you can use the optional DurationSeconds parameter to specify the duration of your session.
You can provide a value from 900 seconds (15 minutes) up to the maximum session duration setting for the role.
This setting can have a value from 1 hour to 12 hours.
Option D is incorrect because the maximum CLI/API session duration should be configured inside the IAM role and not the IDP provider.
Reference:
https://docs.aws.amazon.com/STS/latest/APIReference/API_AssumeRoleWithWebIdentity.html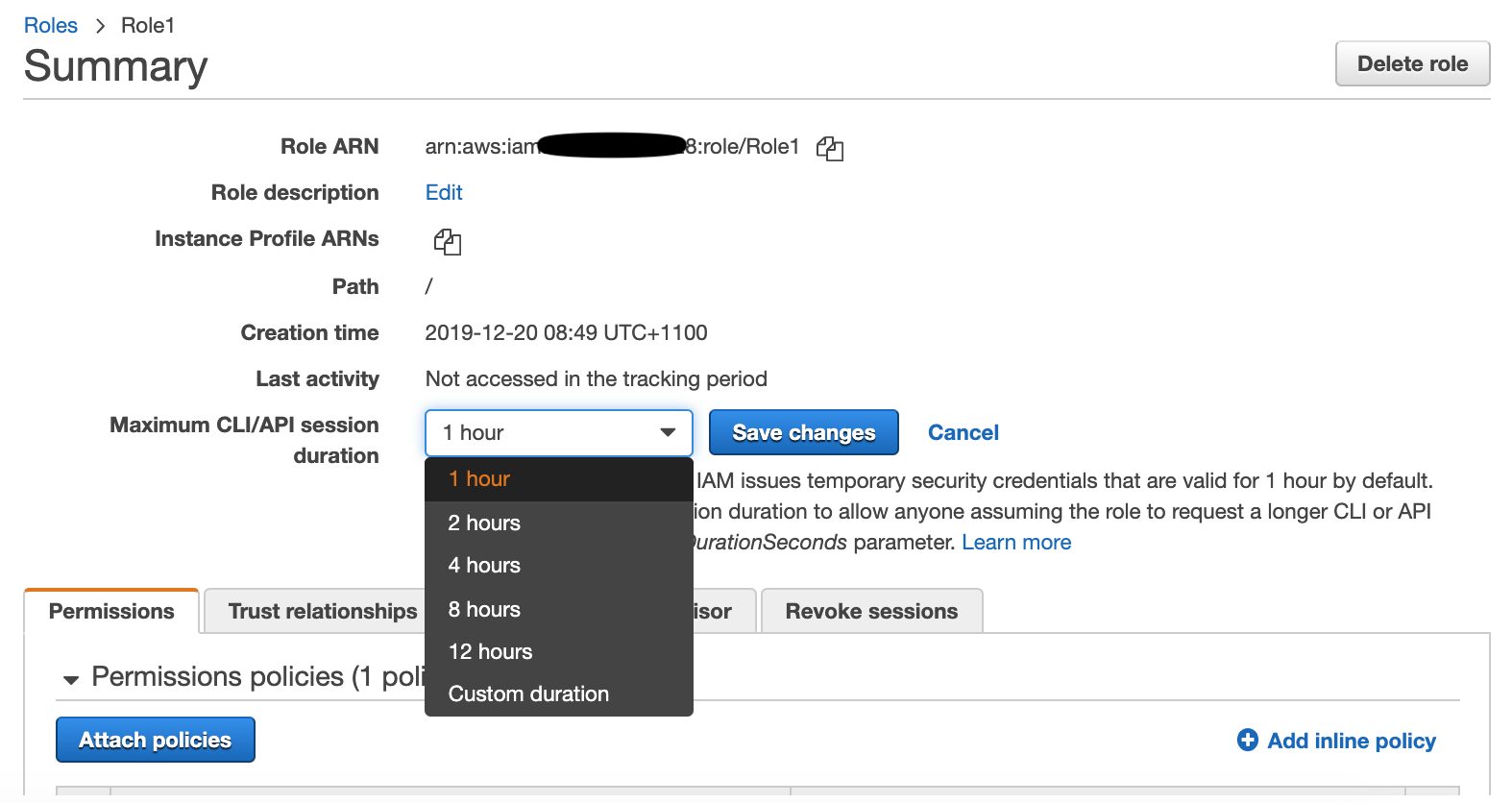
The issue in this scenario is that users are unable to increase the session duration to 2 hours when using the AssumeRoleWithWebIdentity API to access AWS RDS resources. To resolve this problem, we need to understand the factors that impact session duration and how to modify them.
When a user authenticates with an identity provider (IdP) using web identity federation, the IdP issues temporary security credentials to the user. These credentials can be used to access AWS services through an IAM role. The session duration for these credentials is determined by several factors, including the maximum session duration allowed by the IdP, the maximum session duration allowed by the IAM role, and the session duration specified in the AssumeRoleWithWebIdentity API call.
Option A suggests that we should check the maximum session duration setting in the web identity provider. This is a valid step as the maximum session duration allowed by the IdP can impact the session duration of the temporary security credentials. If the maximum session duration is set to less than 2 hours, then the AssumeRoleWithWebIdentity API call will fail when attempting to set the session duration to 2 hours. However, if the maximum session duration is set to greater than or equal to 2 hours, then the issue lies elsewhere.
Option B suggests that the session duration defined in the AssumeRoleWithWebIdentity API is fixed at 1 hour and cannot be modified. This is not true, as the session duration specified in the API call can be modified up to the maximum allowed by the IdP and IAM role.
Option C suggests that the maximum session duration for the IAM role is the limiting factor. This is also a valid step as the maximum session duration allowed by the IAM role can impact the session duration of the temporary security credentials. If the maximum session duration for the IAM role is set to less than 2 hours, then the AssumeRoleWithWebIdentity API call will fail when attempting to set the session duration to 2 hours. However, if the maximum session duration for the IAM role is set to greater than or equal to 2 hours, then the issue lies elsewhere.
Option D suggests that the change needs to be made in the Google identity provider, which is not relevant to this scenario as the identity provider being used is not specified.
In summary, the correct answer is either A or C, depending on which setting is the limiting factor. If the maximum session duration allowed by the web identity provider is less than 2 hours, then we should increase it to allow users to set a session duration of 2 hours. If the maximum session duration allowed by the IAM role is less than 2 hours, then we should increase it to allow users to set a session duration of 2 hours.