Active/Passive Configuration for AWS VPN Connections
Question
When configuring Active/Passive configuration for your VPN connections, which of the following can be used to achieve such a configuration? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and B.
The AWS Documentation mentions this.
multi-data-center-config.
Redundant Active/Active VPN Connections.
Many AWS customers choose to implement VPN connections because they can be a quick, easy, and cost-effective way to set up remote connectivity to a VPC.
Each AWS Virtual Private Gateway (VGW) has two VPN endpoints with capabilities for static and dynamic routing to enable redundancy.
Although statically routed VPN connections from a single customer gateway are sufficient for establishing remote connectivity to a VPC, this is not a highly available configuration.
The best practice for making VPN connections highly available is to use redundant customer gateways and dynamic routing for automatic failover between AWS and customer VPN endpoints.
For simplicity, the diagram in the next section depicts each VPN connection, consisting of two IPsec tunnels to both VGW endpoints, as a single line.
Configuration Details.
The configuration in this example consists of four fully meshed, dynamically routed IPsec tunnels between both VGW endpoints and two customer gateways.
AWS provides configuration templates for several supported VPN devices to assist in establishing these IPsec tunnels and configuring BGP for dynamic routing.
In addition to the AWS-provided VPN and BGP configuration details, customers must configure VPCs to route traffic to their data center networks efficiently.
In this example, the VGW will prefer to send 10.0.0.0/16 traffic to Data Center 1 through Customer Gateway 1 and only reroute this traffic through Data Center 2 if the connection to Data Center 1 is down.
Likewise, 10.1.0.0/16 traffic will prefer the VPN connection originating from Data Center 2.
AWS recommends using one of the following approaches for communicating these route preferences (For a full explanation of the VPC routing rule algorithm, see Configuring Multiple VPN Connections to Your Amazon VPC):
More specific routes: With this approach, both Customer Gateway 1 and Customer Gateway 2 advertise a summary route of 10.0.0.0/15
In addition, Customer Gateway 1 advertises 10.0.0.0/16, and Customer Gateway 2 advertises 10.1.0.0/16
AWS will use the more specific routes to send traffic to the appropriate data center and failback to the other data center following the summarized route if the more specific route becomes temporarily unavailable.
AS-path prepending: With this approach, both Customer Gateway 1 and Customer Gateway 2 advertise 10.0.0.0/16 and 10.1.0.0/16
However, Customer Gateway 1 uses AS-path prepending when advertising the 10.1.0.0/16 network to make this route less preferred.
Likewise, Customer Gateway 2 uses AS-path prepending when advertising the 10.0.0.0/16 network to make this route less preferred.
AWS will use the preferred routes to send traffic to the appropriate data center and will fail back to the other data center following the less preferred routes when necessary.
Option C is incorrect because IPSec is default used as the protocol for communication.
Option D is incorrect because this would not help in this configuration.
For more information on High Availability Network connections, one can visit the below URL.
https://aws.amazon.com/answers/networking/aws-multiple-data-center-ha-network-connectivity/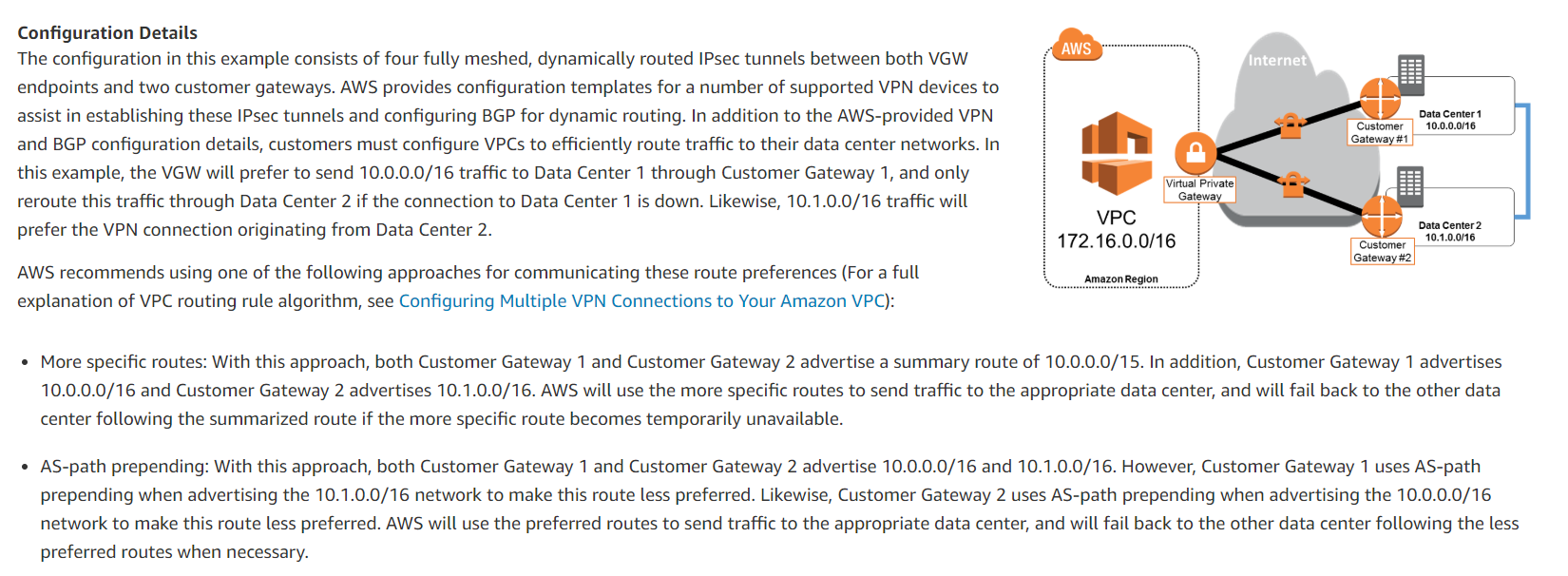
Active/Passive configuration is a setup where two VPN connections are created between the same two endpoints, but only one VPN connection is active at a time, and the other is in standby mode. The standby VPN connection takes over in case the active VPN connection fails.
To achieve this configuration, we can use the following two options:
- Use different ASN numbers:
ASN (Autonomous System Number) is a unique identifier assigned to an autonomous system (AS) in the internet. When two ASNs are different, BGP (Border Gateway Protocol) considers them as separate entities. To configure Active/Passive VPN connections, we can use two different ASN numbers for the two VPN endpoints. We can then use BGP to advertise the same routes with different metrics (using the local preference attribute), one for the active VPN connection and the other for the standby VPN connection. This ensures that traffic flows through the active VPN connection as long as it is operational. If the active VPN connection fails, the standby VPN connection takes over and traffic is routed through it.
- Use more specific routes:
We can also use more specific routes to configure Active/Passive VPN connections. More specific routes have a longer prefix length than the general routes. For example, if we have a general route 10.0.0.0/8, we can create more specific routes like 10.1.0.0/16 and 10.2.0.0/16. We can then configure the active VPN connection to advertise the more specific routes with a higher metric than the standby VPN connection. This ensures that traffic flows through the active VPN connection as long as it is operational. If the active VPN connection fails, the standby VPN connection takes over and traffic is routed through it.
AS_PATH prepending and IPSec routing are not used to configure Active/Passive VPN connections. AS_PATH prepending is a technique used to influence the path selection in BGP by adding the same ASN number multiple times to a BGP route advertisement. IPSec routing is the process of routing traffic through an IPSec tunnel. While both these techniques have their own uses, they are not relevant for configuring Active/Passive VPN connections.