Connectivity Options for Securely Accessing Amazon S3
Question
A large Construction company is storing all design documents in an Amazon S3 bucket.
All these large files are critical project documents that need to access frequently during meetings.
Currently, users are accessing the Amazon S3 bucket over the internet.
Due to performance issues over Internet links, the IT Head is looking for a high-performance, in-transit encrypted link to allow users to access the S3 bucket securely.
Also, he wants to ensure that only Amazon S3 buckets are accessed over these links & no other traffic is allowed on these links.
Which of the following connectivity option meets this requirement in the easiest way?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer - C.
The question asks for the easiest way to solve the requirement given in the question.
Therefore, by limiting the IP ranges of the S3 buckets to be accessed, this can be done easily.
Option A is incorrect as EC2 instance size will add limitations to performance & will be costly due to third-party VPN software on this instance.
Option B is incorrect as S3 by itself supports HTTPS for transport-level encryption.
Refer to page 530 on the below link: https://docs.aws.amazon.com/AmazonS3/latest/dev/s3-dg.pdf
Option D is incorrect as although this will work this will have performance limitations based upon EC2 instance size.
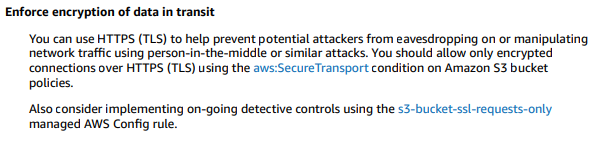
The requirement is to provide a high-performance, in-transit encrypted link to allow users to access the Amazon S3 bucket securely, and ensure that only Amazon S3 buckets are accessed over these links and no other traffic is allowed on these links.
Option A: Use AWS Direct Connect Private VIFs. Use EC2 proxy instance behind a Network Load Balancer to send all traffic towards Amazon S3 using VPC private endpoints.
This option uses Direct Connect Private VIFs, which provides a dedicated, high-bandwidth, and low-latency connection to AWS. This ensures high performance and low latency for accessing the S3 bucket. However, this option requires setting up an EC2 proxy instance behind a Network Load Balancer to send all traffic towards Amazon S3 using VPC private endpoints, which adds complexity to the solution.
Option B: Use a Public VIF, limited to the S3 prefixes, and configure a bucket policy that enforces the use of encryption in transit using the "aws:securetransport" option.
This option uses a Public VIF, which provides a dedicated, high-bandwidth, and low-latency connection to AWS, limited to the S3 prefixes. This ensures that only Amazon S3 buckets are accessed over these links and no other traffic is allowed on these links. Additionally, a bucket policy can be configured to enforce the use of encryption in transit using the "aws:securetransport" option, which ensures that all traffic to and from the S3 bucket is encrypted. However, this option may still suffer from performance issues over the public internet, depending on the location of the users.
Option C: Use AWS Direct Connect Public VIFs. Use route-policy on on-premises routers to allow only Amazon S3 IP range to be accessed.
This option uses Direct Connect Public VIFs, which provides a dedicated, high-bandwidth, and low-latency connection to AWS. Route-policy can be used on on-premises routers to allow only Amazon S3 IP range to be accessed, which ensures that only Amazon S3 buckets are accessed over these links and no other traffic is allowed on these links. However, this option may still suffer from performance issues over the public internet, depending on the location of the users.
Option D: Use software VPN to terminate traffic on Amazon EC2 instance. Use EC2 proxy instance behind a Network Load Balancer to send all traffic towards Amazon S3 using VPC private endpoint.
This option uses a software VPN to terminate traffic on an Amazon EC2 instance. The EC2 instance is then used as a proxy to send all traffic towards Amazon S3 using VPC private endpoint. This option ensures that all traffic is encrypted in transit and only Amazon S3 buckets are accessed over these links. However, this option may suffer from performance issues due to the overhead of VPN encryption and the EC2 instance acting as a proxy.
Based on the requirements, option B is the easiest way to meet the requirement, as it only requires setting up a Public VIF, limited to the S3 prefixes, and configuring a bucket policy that enforces the use of encryption in transit using the "aws:securetransport" option. This option provides a dedicated, high-bandwidth, and low-latency connection to AWS and ensures that only Amazon S3 buckets are accessed over these links, and all traffic to and from the S3 bucket is encrypted.
