Troubleshooting AWS S3 Access Issues in Private Subnets
Question
Your company has a set of instances hosted in a private subnet.
These instances need to make calls to the Simple Storage Service.
You have setup the Endpoint but are still not able to access the S3 buckets from the instances in the private subnet.
Which of the following could be issues for the access? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B and D.
The prefix for the gateway endpoint needs to be added to the Route table.
The below diagram from the AWS Documentation shows the design of an endpoint.
Option A is incorrect because you should use a gateway for S3
Option C is incorrect because the prefix should be attached to the Route table and not the Security Group.
For more information on VPC gateway endpoints , please visit the below URL.
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/vpce-gateway.html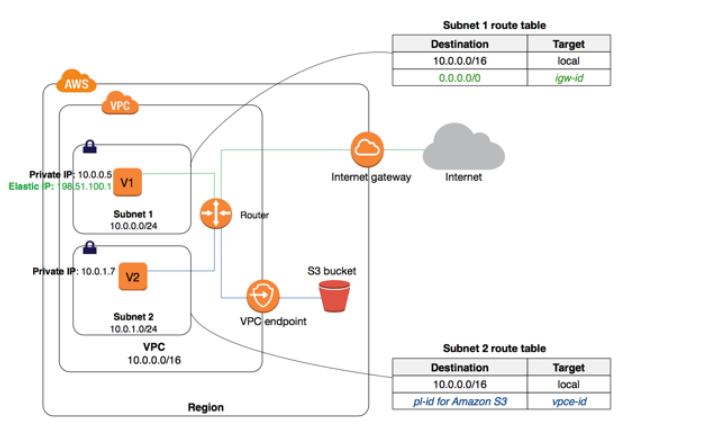
To allow instances in a private subnet to access S3 buckets, you need to set up an S3 VPC endpoint. This creates a connection between the VPC and S3 without requiring the traffic to leave the Amazon network.
If you have set up the S3 VPC endpoint, but instances in the private subnet still can't access the S3 buckets, the following could be the possible issues:
A. You should be using an interface instead of a gateway for accessing the S3 service. An S3 VPC endpoint can be either an interface endpoint or a gateway endpoint. If you created a gateway endpoint, it only supports S3 access from instances in the same Region as the endpoint. If your instances are in a different Region or VPC, you must create an interface endpoint instead.
B. The prefix for the endpoint is not attached to the Route table. To route traffic to the S3 VPC endpoint, you need to add a route to the VPC route table. The route must point to the S3 VPC endpoint's prefix list. If the prefix list is not added to the route table, instances in the private subnet won't know how to route traffic to the S3 VPC endpoint.
C. The prefix for the endpoint is not attached to the Security Group. To allow traffic to flow through the S3 VPC endpoint, you need to add the endpoint's prefix list to the security group rules. This ensures that traffic to and from the S3 VPC endpoint is allowed.
D. Bucket policy attached to S3 buckets doesn't allow access to VPC endpoint. If there is a bucket policy attached to the S3 buckets that restricts access to specific IP addresses, you need to update it to include the S3 VPC endpoint's IP address range. Otherwise, instances in the private subnet won't be able to access the S3 buckets even if the S3 VPC endpoint is set up correctly.
In summary, to troubleshoot issues with accessing S3 buckets from instances in a private subnet with an S3 VPC endpoint set up, you should check whether you are using the correct endpoint type, whether the endpoint's prefix list is added to the VPC route table and security group rules, and whether the bucket policy attached to the S3 buckets allows access from the VPC endpoint's IP address range.