Protecting Against Malicious Requests
Question
Your company has the following setup in AWS. a.
A set of EC2 Instances hosting a web application b.An application load balancer placed in front of the EC2 Instances There seem to be some malicious requests coming from a set of IP addresses.
Which of the following can be used to protect against these requests?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
According to the AWS Documentation,
A web access control list (web ACL) gives you fine-grained control over all of the HTTP(S) web requests that your protected resource responds to.
You can protect Amazon CloudFront, Amazon API Gateway, Application Load Balancer, and AWS AppSync resources.
You can use criteria like the following to allow or block requests:
- IP address origin of the request.
- Country of origin of the request.
- String match or regular expression (regex) match in a part of the request.
- Size of a particular part of the request.
- Detection of malicious SQL code or scripting.
Option A is incorrect because, by default, Security Groups have the Deny policy.
It cannot block a specific set of IP addresses.
Options B and C are incorrect because these services cannot be used to block IP addresses.
For information on AWS WAF Web ACLs, please visit the below URL.
https://docs.aws.amazon.com/waf/latest/developerguide/web-acl.html https://docs.aws.amazon.com/waf/latest/developerguide/how-aws-waf-works.html https://aws.amazon.com/blogs/aws/aws-web-application-firewall-waf-for-application-load-balancers/ https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/distribution-web-awswaf.html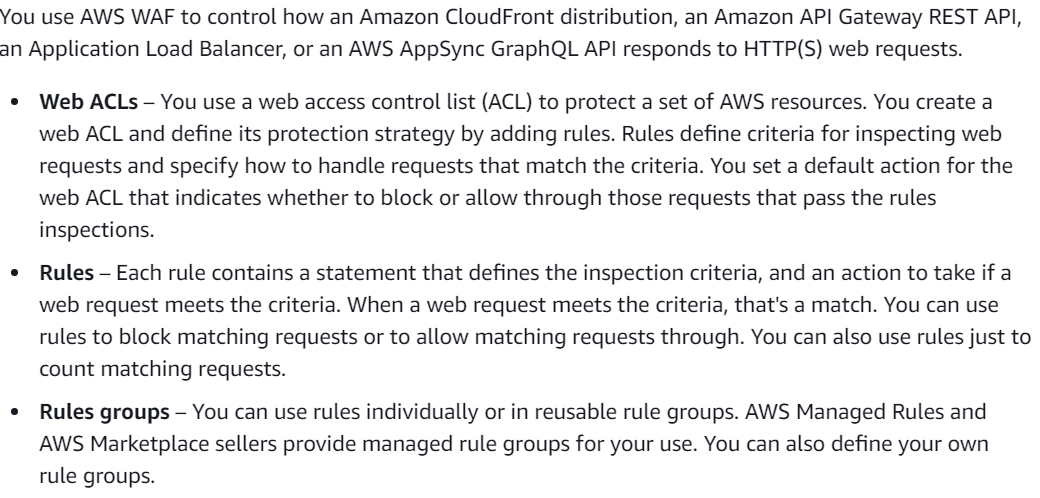
Option D: Use Web ACLs to block the IP addresses is the best choice in this scenario.
Explanation:
AWS Web Application Firewall (WAF) is a service that helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. WAF can monitor and block HTTP/HTTPS traffic based on rules that you configure.
AWS WAF provides a feature called Web ACLs, which allows you to create rules to control the traffic to your web applications. Web ACLs can be associated with Amazon CloudFront distributions, Amazon API Gateway APIs, or Application Load Balancers.
In this scenario, the web application is running behind an Application Load Balancer. By using a Web ACL on the Application Load Balancer, you can block malicious traffic from specific IP addresses, based on rules you configure. This will prevent the malicious traffic from reaching the web application hosted on the EC2 instances.
Option A: Use Security Groups to block the IP addresses is not the best choice in this scenario because Security Groups are used to control inbound and outbound traffic to EC2 instances, whereas the malicious traffic is coming through the Application Load Balancer.
Option B: Use VPC Flow Logs to block the IP addresses is not the best choice in this scenario because VPC Flow Logs can provide visibility into network traffic but are not designed to block traffic.
Option C: Use AWS Inspector to block the IP addresses is not the best choice in this scenario because AWS Inspector is a security assessment service that helps you test the network accessibility of your Amazon EC2 instances and the security state of your applications running on those instances. It is not designed to block traffic.