Which of the below mentioned options is not a valid entry for the main route table in this scenario?
Question
A user has created a VPC with CIDR 20.0.0.0/16 using the wizard.
The user has created a public subnet CIDR (20.0.0.0/24) and VPN only subnets CIDR (20.0.1.0/24) along with the VPN gateway (vgw-12345) to connect to the user's data centre.
The user's data centre has CIDR 172.28.0.0/12
The user has also setup a NAT instance (i-123456) to allow traffic to the internet from the VPN subnet.
Which of the below mentioned options is not a valid entry for the main route table in this scenario?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A.
The below diagram shows how a typical setup for a VPC with VPN and Internet gateway would look like.
The only routing option which should have access to the internet gateway should be the 0.0.0.0/0 address.
So.
Option A is the right answer.
For more information on VPC with the option of VPN, please visit the link:
http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Scenario3.html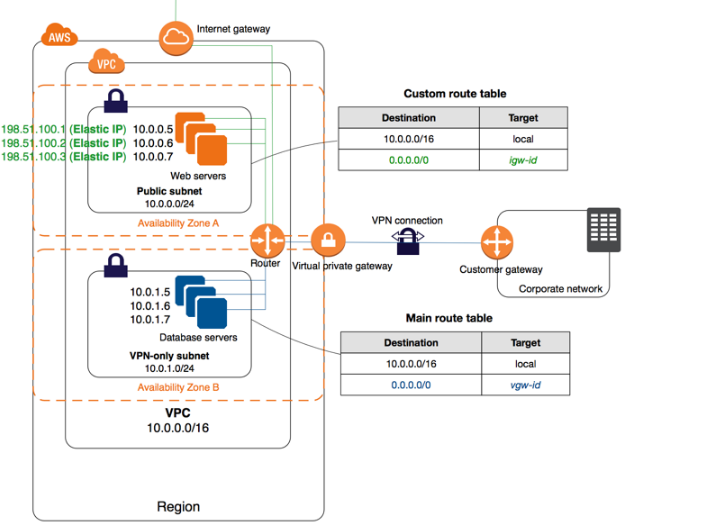
In this scenario, the user has created a VPC with CIDR 20.0.0.0/16 using the wizard. The user has also created a public subnet CIDR (20.0.0.0/24) and VPN only subnets CIDR (20.0.1.0/24) along with the VPN gateway (vgw-12345) to connect to the user's data centre. The user's data centre has CIDR 172.28.0.0/12. The user has also set up a NAT instance (i-123456) to allow traffic to the internet from the VPN subnet.
The main route table is used by default for all subnets in a VPC unless a subnet is explicitly associated with a custom route table. It controls the traffic routing for all the subnets in the VPC that are not explicitly associated with any other custom route table.
Let's check each of the given options to see which one is not a valid entry for the main route table in this scenario:
A. Destination: 20.0.1.0/24 and Target: i-12345
This route entry is valid because it routes traffic for the VPN only subnet (20.0.1.0/24) to the NAT instance (i-12345), which allows traffic to the internet.
B. Destination: 0.0.0.0/0 and Target: i-12345
This route entry is also valid because it routes all traffic (0.0.0.0/0) to the NAT instance (i-12345), which allows traffic to the internet.
C. Destination: 172.28.0.0/12 and Target: vgw-12345
This route entry is also valid because it routes traffic for the user's data centre (172.28.0.0/12) to the VPN gateway (vgw-12345), which connects the VPC to the user's data centre.
D. Destination: 20.0.0.0/16 and Target: local.
This route entry is not valid because it routes all traffic within the VPC (20.0.0.0/16) to the local network interface. However, this is not necessary as the VPC will automatically route traffic within the VPC to the appropriate destination based on the associated subnets and their respective route tables. Therefore, this route entry is redundant and not necessary in the main route table.
In conclusion, the option that is not a valid entry for the main route table in this scenario is D. Destination: 20.0.0.0/16 and Target: local.