How to Set up AWS Account and Grant Access for CloudWatch Events
Question
Your team owns an AWS account for central management.
The AWS accounts from another AWS Organization will send their CloudWatch events to your AWS account's default CloudWatch event bus.
You need to set up your AWS account and grant access to all accounts in that organization so that you can receive the events properly from these AWS accounts.
Which of the following actions is required?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer : D.
Option A is incorrect because on the receiver account, you need to edit the permissions on the default CloudWatch event bus instead of a new IAM role.
Option B is incorrect because you cannot directly attach any IAM policy in CloudWatch Event.
To add the permissions, you should add other AWS accounts or Organization in the event bus.
Option C is incorrect because since the accounts belong to the same organization, you should add the organization ID in the default event bus.
Option D is CORRECT because with this configuration, you have allowed all accounts in the organization to send events to your default event bus.
An example is as follows:
Reference:
https://docs.aws.amazon.com/AmazonCloudWatch/latest/events/CloudWatchEvents-CrossAccountEventDelivery.html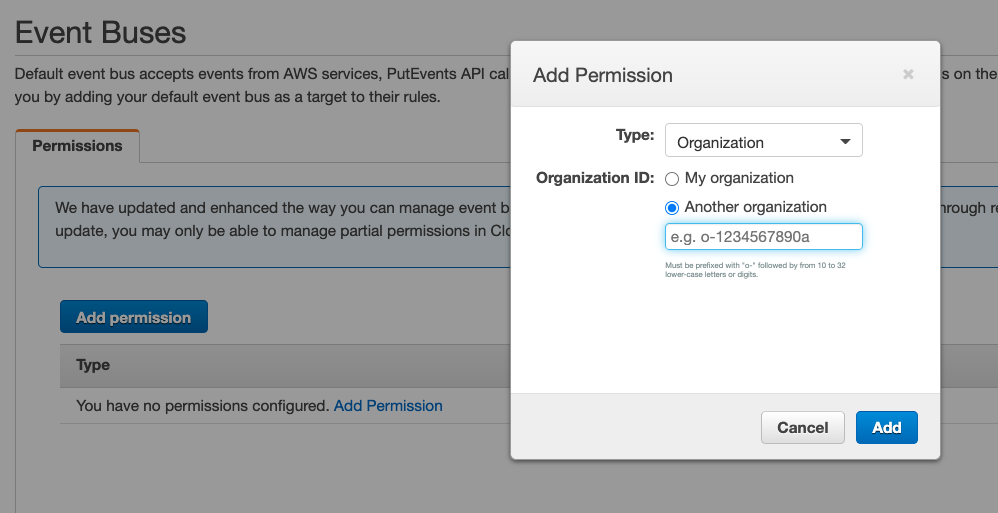
To receive CloudWatch events from AWS accounts in another AWS Organization, you need to set up your AWS account and grant access to those accounts. The correct action required is to create an IAM role in your AWS account that has the permission to send CloudWatch events and allows all accounts in the organization to assume it. Therefore, option A is the correct answer.
Option B is incorrect because attaching an IAM policy in the CloudWatch Event console only applies to events generated within the account, not events generated from external AWS accounts.
Option C is incorrect because adding permission to an event bus does not grant permission to receive events from external accounts.
Option D is also incorrect because the "Organization" option in the "Add Permission" function is for granting permissions to an entire AWS Organization, not to individual accounts within that organization.
To create the IAM role mentioned in option A, you can follow these steps:
In the IAM console, create a new role and choose "Another AWS account" as the trusted entity.
Enter the AWS account ID of the organization in the "Account ID" field.
Attach the "CloudWatchEventsFullAccess" policy to the role.
In the "Permissions" section of the role creation process, create a new inline policy.
Choose "JSON" as the policy editor and enter the following policy:
json{ "Version":"2012-10-17", "Statement":[ { "Effect":"Allow", "Action":"events:PutEvents", "Resource":"*" } ] } This policy allows the AWS accounts in the organization to send events to your default CloudWatch event bus.
- Finally, share the role ARN with the AWS accounts in the organization so that they can assume the role and send events to your event bus.