Detect and Alert Large Traffic Increases | DevOps Engineer Exam Prep
Question
Your public website uses an Application Load Balancer and an Auto Scaling group in a virtual private cloud.
Your chief security officer has asked you to set up a monitoring system that quickly detects and alerts your team when a large sudden traffic increase occurs.
How should you set this up?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answer - D.
The below snapshot from the AWS documentation gives details on the NetworkIn metric.
Please note that Application Load Balancer does not have the NetworkOut metric in CloudWatch so option A is incorrect.
For more information on EC2 metrics, please visit the link:
http://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/ec2-metricscollected.html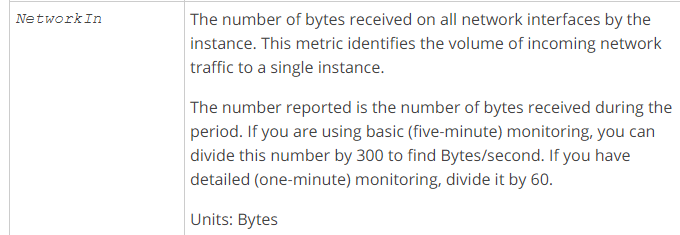
The best answer to this question is A. Set up an Amazon CloudWatch alarm for the Elastic Load Balancing NetworkOut metric and then use Amazon SNS to alert your team.
Explanation:
Option A involves setting up a CloudWatch alarm for the NetworkOut metric associated with the Elastic Load Balancer (ELB). NetworkOut metric measures the amount of data sent from the load balancer to the clients. When traffic increases, this metric also increases. The CloudWatch alarm will trigger when the metric exceeds a specific threshold value, which indicates a sharp increase in traffic.
Once the alarm is triggered, Amazon SNS (Simple Notification Service) can be used to send a notification to the DevOps team. SNS can send notifications to multiple subscribers, including email, SMS, and mobile push notifications. This will quickly alert the team, allowing them to take necessary actions to handle the increased traffic.
Option B involves using Amazon EMR (Elastic MapReduce) to analyze the ELB access logs. This approach is more suitable for batch processing and long-term analysis. Since the question requires a quick detection and alert mechanism, Option B is not the best choice.
Option C involves using Amazon EMR to analyze CloudWatch logs from the application's EC2 instances. However, this approach is less suitable for detecting sudden traffic increases since the logs may not be updated immediately. Moreover, the question requires a quick detection and alert mechanism, which Option C does not provide.
Option D involves setting up a CloudWatch alarm for the NetworkIn metric associated with the EC2 instances of the Auto Scaling group. NetworkIn measures the amount of data received by the instances. Although this metric is related to traffic, it does not directly measure the traffic directed towards the ELB. Hence, Option D may not accurately detect sudden traffic increases.
Option E involves monitoring the CloudTrail logs, which primarily record API calls made to AWS services. CloudTrail logs may not provide accurate information about traffic directed towards the ELB. Hence, Option E is not the best choice.
In conclusion, Option A is the best choice since it involves setting up a CloudWatch alarm for the NetworkOut metric associated with the ELB, which accurately measures traffic directed towards the ELB. Additionally, using SNS notifications allows for quick detection and alert mechanisms.
