Easiest and Cost-Effective Solution for AWS Config Rule Notifications
Question
An AWS security specialist has set up and activated several AWS Config managed rules.
The rules are used to evaluate whether the AWS resources comply with company security policies. For example, Amazon EBS volumes should be encrypted with Customer Managed Keys (CMKs)
If one Config rule becomes non-compliant, the team should get near-real-time notifications. Which option is the easiest one and a cost-effective solution to set up the notifications?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: C.
Option A is incorrect because creating, maintaining, and managing several config rules and integrating with lambda would not be an efficient solution for all the options.
Option B is incorrect because CloudWatch Events can deliver a near real-time stream of system events that describe changes in AWS resources, including AWS Config rules, and using Kinesis would not be the most efficient and cost-effective solution to provide the notification.
Option C is CORRECT because users can configure a CloudWatch Event rule to check the AWS Config compliance change events and integrate with SNS to provide the notifications.
Option D is incorrect because AWS Config rules do not integrate with CloudWatch alarms to notify configuration changes.
Reference:
https://docs.aws.amazon.com/config/latest/developerguide/monitor-config-with-cloudwatchevents.html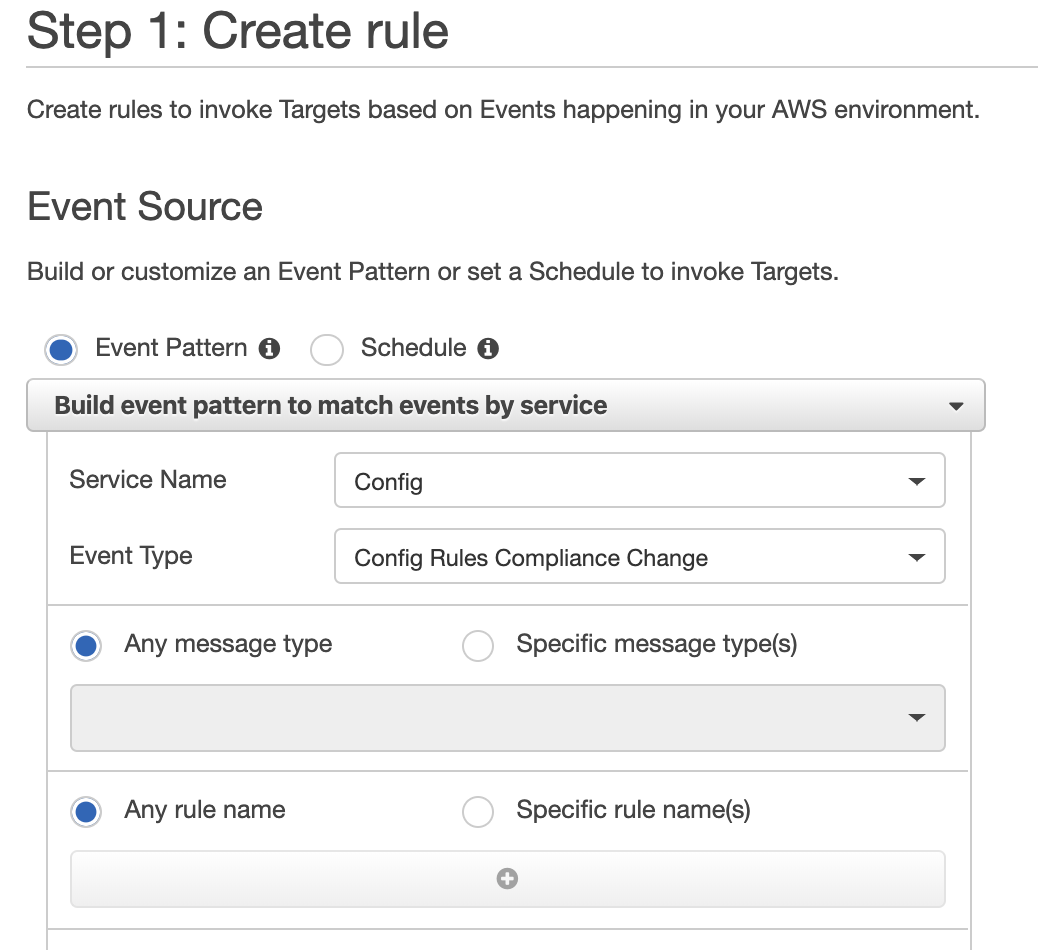
The easiest and most cost-effective solution to set up near-real-time notifications for non-compliant AWS Config rules is Option C: Create an AWS CloudWatch Event rule to check the event type of "Config Rules Compliance Change" and add an SNS topic as the target to provide notifications.
Option A: Configuring AWS Config rules using Lambda functions may work, but it requires additional effort and complexity in setting up Lambda functions and permissions to interact with AWS Config and SNS. Additionally, it could lead to additional costs due to the usage of Lambda functions.
Option B: Integrating AWS Config rules with an Amazon Kinesis stream may provide real-time analysis and notifications, but it is a more complex solution that may require additional effort and infrastructure. This option can be costly, as Kinesis charges for data ingestion, data processing, and data transfer.
Option D: Configuring each AWS Config rule with a CloudWatch alarm may provide a simple solution to send notifications, but it lacks flexibility and scalability. Configuring each rule with a CloudWatch alarm could be time-consuming and lead to higher management overhead. Additionally, it may lead to additional costs due to the usage of CloudWatch alarms.
Option C: Creating an AWS CloudWatch Event rule to check the event type of "Config Rules Compliance Change" and adding an SNS topic as the target to provide notifications is the easiest and most cost-effective solution. The CloudWatch Event rule monitors AWS Config for changes in rule compliance and triggers an SNS notification when a non-compliant event occurs. This option is flexible and scalable as it can handle multiple rules at once and allows the security team to set up granular filtering and notification preferences. Additionally, it provides a cost-effective solution as both CloudWatch Events and SNS are charged on a usage-based model.
