Monitor and Revert Unexpected Changes to AWS EC2 Security Groups
Question
Your company has a set of EC2 Instances in AWS.
These EC2 Instances have strict security groups attached to them.
You need to ensure that unexpected changes to the security groups are monitored and reverted.
How can you achieve this?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - D.
The below diagram from an AWS blog shows how security groups can be monitored.
Option A is incorrect because the method cannot revert the change in real-time.
Compared with Option D, this one is more complicated too.
Option B is incorrect because CloudWatch metrics cannot be used to check the change of security groups.
Option C is incorrect because AWS Inspector is not used to monitor the activity of security groups.
For more information on monitoring security groups, please visit the below URL:
https://aws.amazon.com/blogs/security/how-to-automatically-revert-and-receive-notifications-about-changes-to-your-amazon-vpc-security-groups/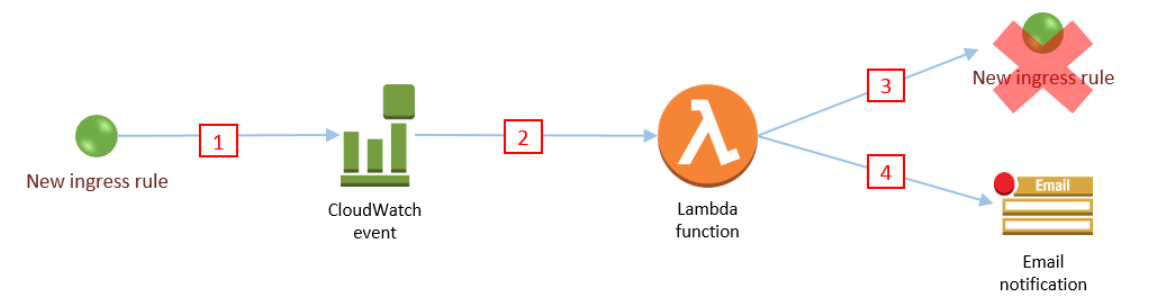
To ensure that unexpected changes to the security groups on your EC2 instances are monitored and reverted, you can use the following steps:
Use CloudTrail to track changes to security groups: AWS CloudTrail is a service that records API calls made on your AWS account. By enabling CloudTrail on your account, you can track all changes made to your security groups. This includes any modifications made to the rules, the addition or removal of a security group, and other security-related activities.
Create a CloudWatch Event Rule to monitor changes: With CloudTrail enabled, you can create a CloudWatch event rule to monitor changes to your security groups. This rule will trigger an AWS Lambda function whenever a security group is modified.
Configure a Lambda function to revert the changes: The AWS Lambda function that is triggered by the CloudWatch event rule can be used to revert any changes made to the security groups. The function can be configured to retrieve the previous rules for the security group and restore them. This ensures that your security groups always maintain their intended configuration.
Configure notifications: You can configure your Lambda function to send an email notification to the security team whenever a security group is modified. This provides the team with information about the change and allows them to take any additional action if required.
Based on the given answer options, option D is the correct answer, as it covers all the necessary steps to monitor and revert unexpected changes to the security groups on your EC2 instances. Option A only covers step 1 and 3, while option B and C do not cover all the necessary steps.