Identifying Security Group Access
Question
Your company has defined a number of EC2 Instances.
They want to know if any of the security groups allow unrestricted access to a resource.
Which of the following provides the SIMPLEST solution to accomplish the requirement?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer is B.
Option A is incorrect because AWS Inspector is used for detecting security vulnerabilities in an instance and not for security groups.
Option B is CORRECT because AWS Trusted Advisor can check security groups for rules that allow unrestricted access to a resource.
Option C is incorrect because AWS Config is used to detect changes in security groups but not show you security groups that have compromised access.
Option D is incorrect since it offers a partially correct solution and also would create a maintenance overhead with additional filtering activities.
Below snapshot provides an overview of AWS Trusted Advisor and the details it provides with regards to your AWS account.
For more information on the AWS Trusted Advisor, please visit the below URL:
https://aws.amazon.com/premiumsupport/trustedadvisor/best-practices/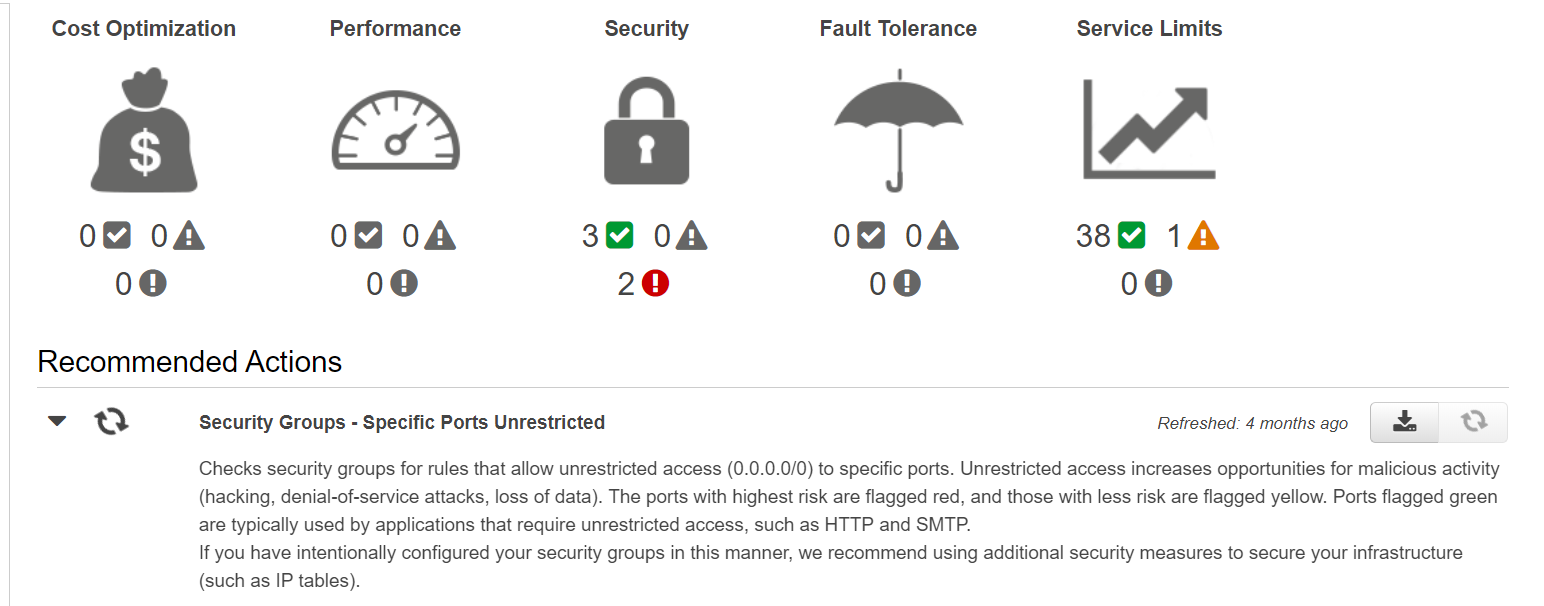
The simplest solution to identify which security groups allow unrestricted access to a resource is to use the AWS CLI to query the security groups and filter the rules for unrestricted access. Option D is the correct answer.
Option A, using AWS Inspector, is a tool that helps to identify security issues in EC2 instances and applications running on them. However, it is not the appropriate tool to identify security group rules.
Option B, using AWS Trusted Advisor, is a tool that provides recommendations to optimize AWS resources, including security groups. However, it does not specifically identify security groups that allow unrestricted access.
Option C, using AWS Config, is a tool that provides a detailed inventory of AWS resources and their configurations, including security groups. It can be used to identify non-compliant security group rules. However, it requires additional configuration to specifically identify security groups that allow unrestricted access.
Option D, using the AWS CLI, is a command-line interface that allows developers to interact with AWS services using scripts or commands. The describe-security-groups command can be used to retrieve information about security groups, and the --query parameter can be used to filter the results. For example, the following command can be used to identify security groups with unrestricted access to port 22:
markdownaws ec2 describe-security-groups --query 'SecurityGroups[?IpPermissions[?FromPort=='22' && ToPort=='22' && IpRanges[?CidrIp=='0.0.0.0/0']].GroupId]' This command retrieves the security group ID for any security group that has an inbound rule allowing unrestricted access to port 22.
In summary, using the AWS CLI to query and filter security group rules provides the simplest solution to identify security groups that allow unrestricted access to a resource.
