How to Configure Amazon RDS MySQL with HTTPS and VPC Subnets
Question
A company hosts a popular web application that connects to an Amazon RDS MySQL DB instance running in a default VPC private subnet with NACL settings that was created by AWS as default.
The web servers must be accessible only to customers on HTTPS connections, and the database must only be accessible to web servers in a public subnet.
Which solution would meet these requirements without impacting other applications? (SELECT TWO)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Correct Answer - B and C.
This sort of setup is explained in the AWS documentation.
1) To ensure that traffic can flow into your webserver from anywhere on secure traffic, you need to allow inbound security at 443.
2) And then, you need to ensure that traffic can flow from the webserver to the database server via the database security group.
The below snapshots from the AWS Documentation show rule tables for security groups related to the same requirements as in the question.
For more information on this use case scenario, please visit the following URL:
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Scenario2.htmlOptions A and D are invalid answers.
Network ACLs are stateless.
So we need to set rules for both inbound and outbound traffic for Network ACLs.
Option E is also invalid because, in order to communicate with the MySQL servers, we need to allow traffic to flow through port 3306.
Note: The above correct options are the combination of steps required to secure your web and database servers.
Besides, the company may implement additional security measures from their end.
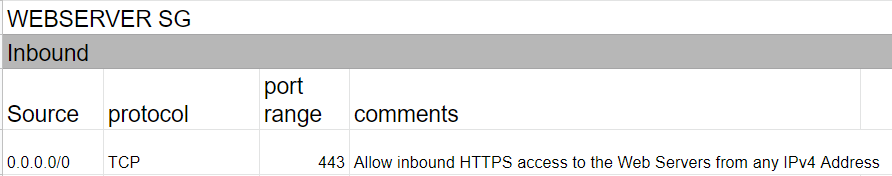
To meet the given requirements, we need to allow HTTPS traffic to the web server and restrict access to the database server to only the web servers in a public subnet. We can achieve this by implementing the following solutions:
A. Create a network ACL on the Web Server's subnets, allow HTTPS port 443 inbound and specify the source as 0.0.0.0/0. This option allows incoming HTTPS traffic from anywhere, which is not recommended as it could open up the web server to attacks from unauthorized sources. Therefore, this option is not recommended.
B. Create a Web Server security group that allows HTTPS port 443 inbound traffic from anywhere (0.0.0.0/0) and apply it to the Web Servers. This option allows incoming HTTPS traffic only to the web server and restricts access from unauthorized sources. It is a recommended solution.
C. Create a DB Server security group that allows MySQL port 3306 inbound and specify the source as the Web Server security group. This option allows incoming traffic to the database server only from the web server security group, which restricts access from unauthorized sources. It is a recommended solution.
D. Create a network ACL on the DB subnet, allow MySQL port 3306 inbound for Web Servers and deny all outbound traffic. This option allows incoming traffic to the database server only from the web server and restricts outbound traffic from the database server. However, it does not restrict access from other sources, which makes it an incomplete solution. Therefore, it is not a recommended solution.
E. Create a DB Server security group that allows HTTPS port 443 inbound and specify the source as a Web Server security group. This option allows incoming HTTPS traffic only to the database server and restricts access from unauthorized sources. However, it does not restrict access to the MySQL port, which is required to access the database server. Therefore, it is not a recommended solution.
In conclusion, options B and C are the recommended solutions to meet the given requirements. Option B restricts incoming traffic to HTTPS traffic only, and option C restricts access to the database server only from the web server security group.