Troubleshooting Inaccessible Application
Question
Your company is hosting a web application on AWS (with an autoscaling group already in place)
According to the architectural best practices, the application must be highly available, scalable, cost-effective, with high-performance, and require minimal human intervention.
You have deployed the web servers and database servers in the public and private subnet of the VPC, respectively.
While testing the application via a web browser, you noticed that the application is not accessible.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answers - C.
Option A is incorrect because (a) NAT instance is ideally used to route traffic from a private subnet to the internet via a public subnet, (b) NAT instance is not managed by AWS and requires to be configured and maintained by the user; hence, adding to the overhead, and (c) if not scaled, can cause a performance bottleneck.
NAT Gateway is a preferred option over NAT instances.
Option B recommends using AWS CloudFront and configure the distributions Origin to the web server and then use an AWS Route 53 ‘CNAME' for the CloudFront Distribution.
CloudFront is highly available and accessible to the Internet.
It would work better if the Origin for the AWS CloudFront Distribution were pointed to an AWS ELB rather than the Web Server itself.
CloudFront doesn´t support IPs as origins.
Since the Origin would only be a Web Server, if this server goes offline for a period of time, the website would become unavailable.
The content is not cached at the Edge location or if the TTL for the content expires.
So, Option B is incorrect as well.
Option C is CORRECT.
Because, (a) if the web servers are behind an ELB, the load on the web servers will be uniformly distributed.
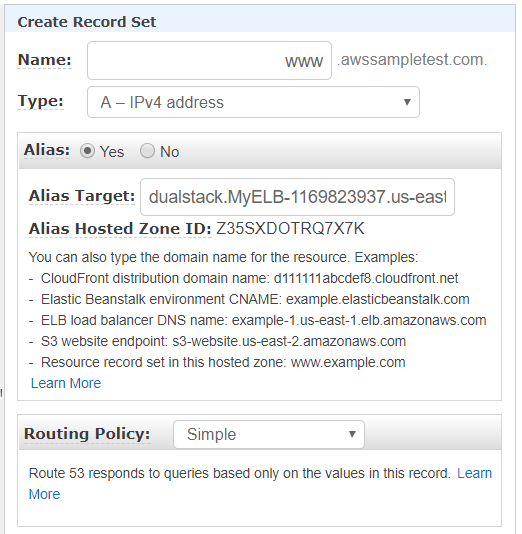
Hence, if any of the web servers goes offline or becomes non-responsive, the traffic would be routed to other online web servers; making the application highly available, and (b) You can use Route53 to set the ALIAS record that points to the ELB endpoint.
Option D is incorrect.
Because the Auto Scaling group may terminate and relaunch a new instance.
It is not suitable to configure the recordset that points to EIPs.
Sure, I'd be happy to explain the options for resolving the issue you are facing with the web application not being accessible.
Option A: Configure a NAT instance in your VPC and create a default route via the NAT instance and associate it with all subnets. Configure a DNS A record that points to the NAT instance public IP address.
In this option, a NAT instance will be deployed in your VPC and all traffic from the private subnet to the Internet will be routed through this NAT instance. A default route will be configured to point to the NAT instance, and all subnets will be associated with this route. In addition, a DNS A record will be created that points to the public IP address of the NAT instance.
This option will enable the web application to access the Internet and provide external users with access to the application. However, it does not provide a high level of availability since the NAT instance can be a single point of failure. Moreover, it may not be the most cost-effective option since you will need to pay for the NAT instance.
Option B: Configure a CloudFront distribution and configure the origin to point to the private IP addresses of your Web servers. Configure a Route53 CNAME record to your CloudFront distribution.
In this option, a CloudFront distribution will be created to cache and serve static content from the web application. The origin for the CloudFront distribution will be configured to point to the private IP addresses of the web servers. A Route53 CNAME record will be created to point to the CloudFront distribution.
This option provides a high level of availability since the CloudFront distribution is replicated across multiple availability zones. It also improves the performance of the application by caching static content closer to the users. However, it may not be the most cost-effective option since you will need to pay for the CloudFront distribution.
Option C: Place all your web servers behind ELB.
In this option, all web servers will be placed behind an Elastic Load Balancer (ELB). The ELB will distribute incoming traffic across all web servers and provide health checks to ensure that only healthy web servers receive traffic.
This option provides a high level of availability since the ELB is replicated across multiple availability zones. It also improves the performance of the application by distributing traffic across multiple web servers. However, it may not be the most cost-effective option since you will need to pay for the ELB.
Option D: Configure a Route53 ALIAS-Record to point to the ELB DNS name.
In this option, a Route53 ALIAS record will be created to point to the DNS name of the ELB. The ALIAS record will resolve to the IP address of the ELB, and traffic will be distributed across all web servers.
This option provides a high level of availability since the ELB is replicated across multiple availability zones. It also simplifies DNS management since the Route53 ALIAS record automatically resolves to the IP address of the ELB. However, it may not be the most cost-effective option since you will need to pay for the ELB.
Option E: Assign EIPs to all web servers. Configure a Route53 A-Record set with all EIPs with health checks and DNS failover.
In this option, Elastic IP addresses (EIPs) will be assigned to all web servers. A Route53 A-Record set will be created with all EIPs and health checks will be configured to monitor the health of the web servers. DNS failover will be configured to automatically route traffic to healthy web servers in the event of a failure.
This option provides a high level of availability since it ensures that traffic is always routed to a healthy web server. It also provides cost savings since there is no need to pay for additional services like ELB or CloudFront.
