Enabling On-Premises Credentials for AWS Management Console Access
Question
Company ABC has used on-premises AD administrative tools to manage resources.
The company wants to enable all employees to use on-premises credentials to sign in to the AWS Management Console to access and manage its various AWS resources (e.g., AWS Workspaces etc..) To achieve this, they have successfully created an AWS Microsoft AD directory connected to their on-premises AD via a forest trust relationship.
Which below items are still required? Select 3.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Correct Answer - C, D, E.
Using AWS Managed Microsoft AD directory, you can easily enable access to multiple AWS applications and services such as the AWS Management Console, Amazon WorkSpaces, and Amazon RDS for SQL Server.
More importantly, your users can access the application or service with their existing AD credentials.
Refer to https://aws.amazon.com/blogs/security/how-to-access-the-aws-management-console-using-aws-microsoft-ad-and-your-on-premises-credentials/ on the details on how to setup AWS Managed Microsoft AD directory and manage administrative permissions to AWS resources.
Option A is INCORRECT because Systems Manager provides a unified user interface so you can view operational data from multiple AWS services and is not used to provide access to AWS instances for on-premise users.
Option B is incorrect: Because NACL ( Network Access Control List ) belongs to the scope of subnets.
In this case, the security group of the AWS Microsoft AD directory should be taken care of.
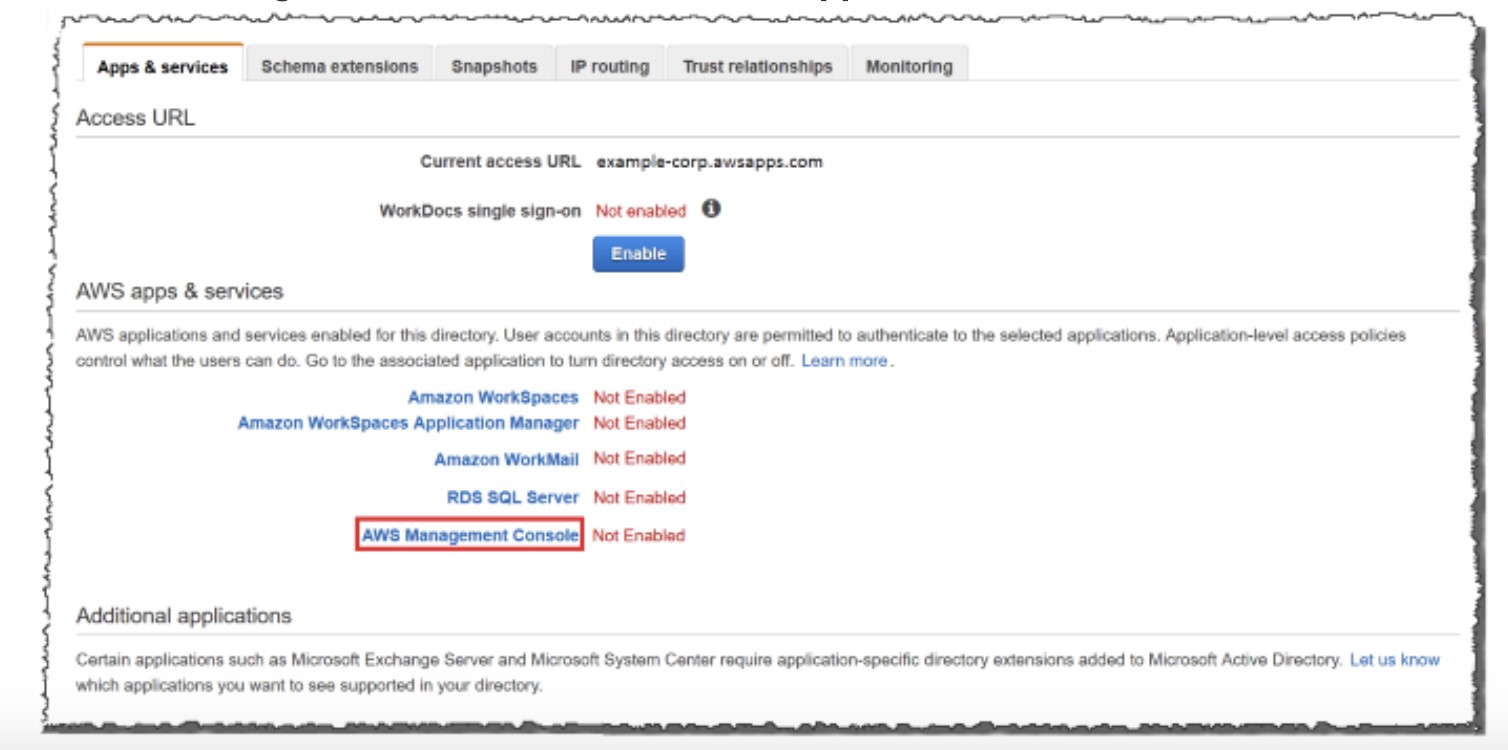
Option C is CORRECT because we need to access all services like the AWS Workspaces, AWS WorkMail, AWS Console, and RDS.
The access to the management console can be enabled as given below.
Option D is CORRECT: Because this enables AWS Management Console access and provides a URL that can be used to connect to the console.
The URL is generated by appending “/console” to the end of the access URL generated in Option.
C.Option E is CORRECT: Because this critical step is used to control which AWS resources on-premises users and groups can access from the AWS Management Console.
The correct answers are A, B, and E.
A) Configure AWS System Manager to provide access to AWS instances for on-premise users: This step is required because it enables on-premises users to access AWS resources that are running on EC2 instances. AWS System Manager is a service that allows you to manage resources on EC2 instances and on-premises servers. By configuring AWS System Manager, on-premises users will be able to access EC2 instances and perform actions like patching, executing scripts, and managing resources.
B) Ensure the NACL of the AWS Microsoft AD directory allows the outbound traffic to on-premise AD tools: This step is necessary to allow on-premises AD tools to communicate with the AWS Microsoft AD directory. Network Access Control Lists (NACLs) are used to control inbound and outbound traffic at the subnet level. By ensuring that the NACL of the AWS Microsoft AD directory allows outbound traffic to on-premise AD tools, the on-premises AD tools can communicate with the AWS Microsoft AD directory and authenticate users.
C) In AWS apps & services section for the AWS Microsoft AD directory, enable all services: This step is not required to achieve the goal of allowing on-premises users to use their credentials to sign in to the AWS Management Console. However, it is necessary to enable specific AWS services like Amazon WorkSpaces, Amazon WorkMail, RDS SQL Server, and AWS Management Console. By enabling these services, on-premises users can access and manage these AWS resources using their on-premises credentials.
D) Enable AWS Management Console access for the AWS Microsoft AD directory and get the URL that can be used to connect to the console: This step is necessary to allow on-premises users to access and manage AWS resources using the AWS Management Console. By enabling AWS Management Console access for the AWS Microsoft AD directory and getting the URL that can be used to connect to the console, on-premises users can use their on-premises credentials to sign in to the AWS Management Console and access and manage various AWS resources.
E) Assign on-premises users and groups to IAM roles: This step is required to grant on-premises users access to AWS resources. IAM (Identity and Access Management) is a service that allows you to manage access to AWS resources. By assigning on-premises users and groups to IAM roles, you can grant them access to specific AWS resources and limit their access based on their job responsibilities.