Troubleshooting: Modifying Amazon VPC Subnet Route Table for VPN Connection Issue
Question
An organization is trying to establish a static VPN connection between an on-premises network and an Amazon VPC.
A SysOps Administrator has created the virtual private gateway., VPN connection, and the customer gateway.
The customer side of the router is also configured, and the connection status shows UP in the console.
However, when the Administrator attempts to connect an Amazon EC2 instance in the Amazon VPC from one of the on-premises virtual machines, it does not work. How should the route table in the Amazon VPC subnet be modified to remediate the issue?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: A.
The below diagram from the AWS Documentation shows that the route needs to be added for the Virtual private gateway.
The above diagram shows the routing for a VPC with an internet gateway, a virtual private gateway, a public subnet, and a VPN-only subnet.
The main route table has a route to the virtual private gateway.
A custom route table is explicitly associated with the public subnet.
The custom route table has a route to the internet (
0.0.0.0/0
) through the internet gateway.
If you create a new subnet in this VPC, it's automatically implicitly associated with the main route table, which routes traffic to the virtual private gateway.
If you set up the reverse configuration (where the main route table has the route to the internet gateway, and the custom route table has the route to the virtual private gateway), then a new subnet automatically has a route to the internet gateway.
All other options are incorrect since the main reason is that the Route table is not attached to the virtual private gateway.
For more information on Route Tables, please visit the below URL-
https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html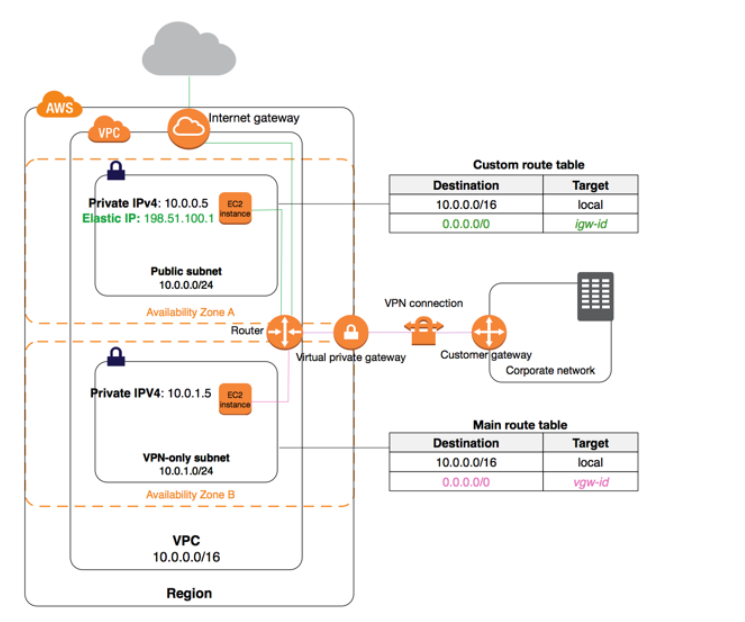
When establishing a VPN connection between an on-premises network and an Amazon VPC, it is important to configure the route tables correctly to ensure proper connectivity. In this scenario, the connection status shows UP in the console, indicating that the VPN connection is established successfully, but the Amazon EC2 instance cannot be accessed from the on-premises virtual machine.
To remediate the issue, the route table in the Amazon VPC subnet needs to be modified. The route table is responsible for directing network traffic to its intended destination, and in this case, it needs to be modified to include a route for the on-premises network.
The correct answer is A. Add the route for the virtual private gateway.
Explanation: The virtual private gateway is the endpoint on the Amazon VPC side of the VPN connection. Adding a route for the virtual private gateway in the Amazon VPC subnet's route table tells the subnet to direct traffic intended for the on-premises network to the virtual private gateway. This ensures that traffic from the on-premises network can reach the Amazon VPC and vice versa.
Option B, adding a route for the VPC endpoint, is incorrect because VPC endpoints are used for accessing AWS services over a private connection, and not for establishing VPN connections.
Option C, adding a route to the internet gateway, is incorrect because it would route traffic intended for the on-premises network to the internet instead of through the VPN connection.
Option D, adding a route for the customer gateway, is also incorrect because the customer gateway is already configured and the connection status shows UP in the console, indicating that the customer gateway is working properly.