Workload Impact of CMK Rotation | AWS Certified SysOps Administrator - Associate
Question
For a three-tier application, data in AWS RDS and application data in Amazon EBS volumes are encrypted using AWS KMS.
The security team has been instructed to rotate CMKs by enabling automated key rotation to comply with security guidelines.
Management is concerned about workload post-rotation of CMKs. Which of the following is TRUE with respect to rotation of CMK?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: A.
Automatic key rotation for CMKs in AWS KMS changes the cryptographic material used in the encryption of keys.
This will only change the backing key for the new CMK, and the old CMK is retained as it is.
With automated key rotation, there is no need to make changes to applications that refer to old keys.
All the key properties will remain the same post rotation of CMK.
Option B is incorrect as there would not be any change in Key ID post rotation of CMK.
Option C is incorrect as data encrypted by Old CMK is decrypted using the same CMK.
No need to re-encrypt this data using the new CMK.
Option D is incorrect as Rotating CMK has no impact on data keys.
For more information on Rotating Keys using AWS KMS, refer to the following URL,
https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html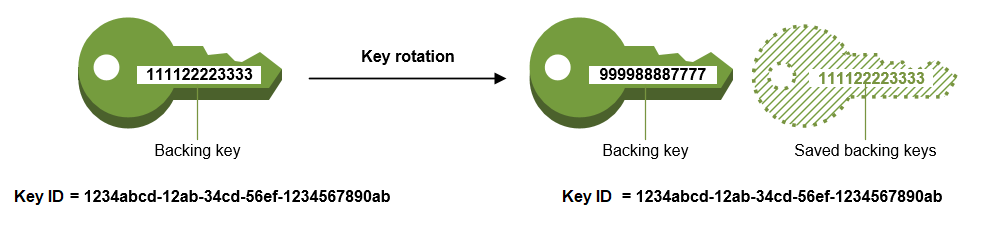
Sure, I'll be happy to help you understand the concepts behind rotating CMKs in AWS KMS.
First, let's define what a Customer Master Key (CMK) is. In AWS KMS, a CMK is a logical representation of a cryptographic key that is used to encrypt and decrypt data. A CMK can be created and managed using the AWS Management Console, AWS CLI, or AWS SDKs.
Rotating a CMK refers to the process of automatically replacing the current CMK with a new CMK, while retaining the same key material. This is typically done as a security measure to reduce the risk of a compromised key being used to access sensitive data.
Now let's go through the options one by one:
A. Rotating CMK will change the backing key.
This is incorrect. When a CMK is rotated, the underlying key material remains the same. The only thing that changes is the key identifier (also known as the Key ID), which is used to reference the CMK.
B. Rotating CMK will need to change in Key ID referred by an application using this CMK.
This is partially correct. When a CMK is rotated, the Key ID will change, so any applications that reference the old Key ID will need to be updated to use the new Key ID. This can be done programmatically using the AWS SDKs or manually through the AWS Management Console.
C. Rotating CMK will re-encrypt data encrypted by the old CMK.
This is incorrect. When a CMK is rotated, the data encrypted using the old CMK can still be decrypted using the new CMK, as long as the key material remains the same. Therefore, data does not need to be re-encrypted after a CMK rotation.
D. Rotating CMK will rotate Data Keys automatically which the old CMK generated.
This is incorrect. When a CMK is rotated, the existing Data Keys generated using the old CMK can still be used to decrypt data, as long as the key material remains the same. Therefore, Data Keys do not need to be rotated after a CMK rotation.
In conclusion, the correct answer is B. Rotating a CMK will require updating the Key ID referred by any application using the old CMK to the new Key ID of the rotated CMK.