Secure Database Deployment with CloudFormation
Question
You are in charge of developing Cloudformation templates that would be used to deploy databases in different AWS Accounts.
To ensure that the passwords for the database are passed in a secure manner, which of the following could you use with Cloudformation?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - C.
The AWS Documentation mentions the following.
Option A is incorrect since this is used to describes the values that are returned whenever you view your stack's properties.
Option B is incorrect since this is used to specify Objects that provide additional information about the template.
Option D is incorrect since here you would need to add the hard-coded passwords.
For more information on best practices for Cloudformation, please refer to the below URL-
https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/best-practices.html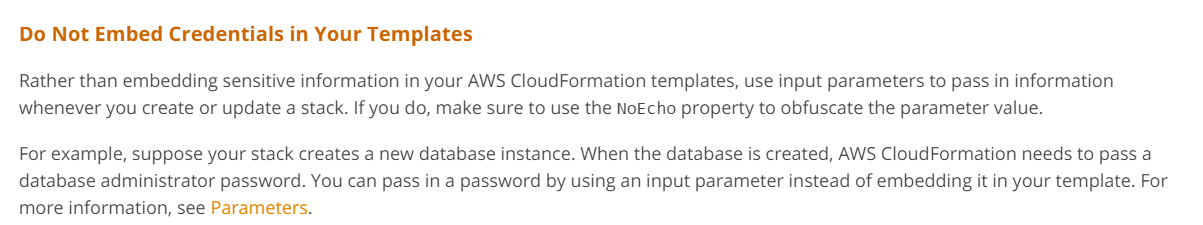
To ensure that the passwords for the database are passed in a secure manner with CloudFormation, you can use parameters.
Parameters are variables that are passed to the CloudFormation stack at runtime. Parameters enable you to specify inputs to your template when you create or update a stack. With parameters, you can pass values such as passwords, AMI IDs, and instance types to your template.
By using parameters to pass passwords, you can ensure that they are not hard-coded in your template, which would make them visible to anyone who has access to your template. Instead, you can prompt users for the password when they launch the CloudFormation stack, or you can store the password in AWS Systems Manager Parameter Store or AWS Secrets Manager and retrieve it at runtime.
Outputs, metadata, and resources are not designed to be used for passing passwords securely. Outputs are used to export values from your stack, metadata is used to provide additional information about your template, and resources are used to define the AWS resources that you want to create with your stack.
Therefore, the correct answer is C. Parameters.