Get SSH Key as User Input
Question
A designer is preparing for a demo to the development lead.
He is using a Cloudformation template as the template could be version controlled.
He wants the template to be able to get the SSH Key as a user input in order to SSH to an EC2 instance that will be created by the Cloudformation stack later on.
Which below approach is the proper one to make this happen?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Corrrect Answer: B.
You can author AWS CloudFormation templates in JSON or YAML formats.
The optional Parameters section is used to customize your templates.
Parameters enable you to input custom values to your template each time you create or update a stack.
You use the Ref intrinsic function to reference a parameter, and AWS CloudFormation uses the parameter's value to provision the stack.
You can reference parameters from the Resources and Outputs sections of the same template.
The below is an example of using “MyKeyPair” as a parameter:
Option A is incorrect: because XML cannot be used for Cloudformation template.
Option C is incorrect: because the keyword to refer to parameter is “Ref” rather than “Reference”.
Option D is incorrect: because for Parameter, the type should be a string for this case.
The type of “Key” is wrong.
XML also cannot be used for Cloudformation template.
Please refer to https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/parameters-section-structure.html for the structure of parameter section.
Other than that, to use the parameter for instances, the “Ref” should be put into “Properties” section rather than “Metadata”.
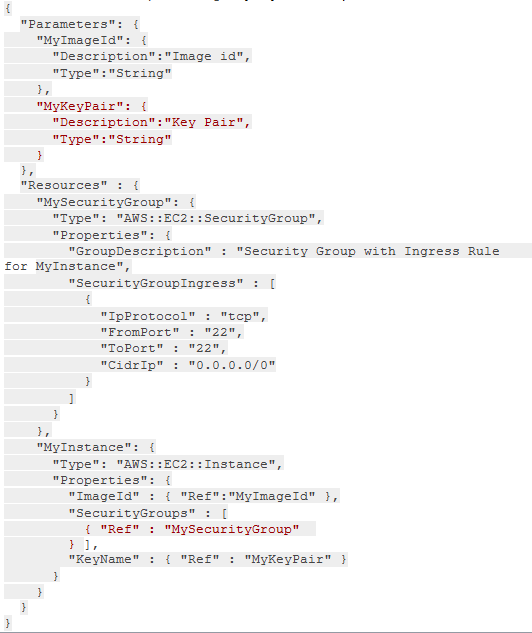
The correct approach to allow the CloudFormation template to get the SSH key as a user input in order to SSH to an EC2 instance that will be created by the CloudFormation stack later on is option B.
Option A is incorrect because CloudFormation templates are written in JSON or YAML format, not XML format.
Option C is partially correct, but it includes a mistake. The keyword to refer to a parameter in CloudFormation templates is not "Reference", but "Ref".
Option D is also partially correct, but it includes some mistakes. CloudFormation templates are typically written in JSON or YAML format, not XML format. Additionally, the "Type" of the "MyKeyPair" parameter should be set to "AWS::EC2::KeyPair::KeyName", not "Key". The Metadata section is not the correct place to refer to the "MyKeyPair" parameter either. Instead, the "KeyName" property of the "AWS::EC2::Instance" resource should be set to the "MyKeyPair" parameter using the "Ref" function.
Option B is the correct approach. It recommends using an editor to write a template using JSON or YAML, and adding a parameter section for the SSH Key, such as "MyKeyPair". The "Ref" function is used to refer to this parameter for new instances. The template is then saved in S3 and uploaded during stack creation.
To expand on this approach, here are some additional steps that could be taken:
In the CloudFormation template editor, create a new template in either JSON or YAML format.
Add a "Parameters" section to the template, and define a parameter for the SSH key, such as "MyKeyPair". Specify the "Type" of this parameter as "AWS::EC2::KeyPair::KeyName". This will ensure that CloudFormation validates that the input provided for this parameter is an existing EC2 key pair name.
Example:
rustParameters: MyKeyPair: Type: AWS::EC2::KeyPair::KeyName Description: The name of an existing EC2 key pair to use for SSH access to the EC2 instances. - When defining the "AWS::EC2::Instance" resource in the template, use the "KeyName" property to specify the SSH key pair to use for the instance. The value of this property should be set to the "MyKeyPair" parameter using the "Ref" function.
Example:
yamlResources: MyEC2Instance: Type: AWS::EC2::Instance Properties: ImageId: ami-0c55b159cbfafe1f0 InstanceType: t2.micro KeyName: !Ref MyKeyPair Save the CloudFormation template in an S3 bucket, and make sure the bucket is accessible to the AWS account where the stack will be created.
Create the CloudFormation stack using the saved template. During the stack creation process, specify the value of the "MyKeyPair" parameter. This value will be used for all instances created by the stack.
By following this approach, the CloudFormation template will be able to get the SSH key as a user input, and use it to SSH into the EC2 instances created by the stack. This approach also provides the benefits of version control and reusability that come with using CloudFormation templates.