Prevent DDoS Attacks with AWS CloudFront
Question
A company is planning on using AWS EC2 and AWS CloudFront for its web application.
For which one of the below attacks is the usage of CloudFront most suited?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: C.
Options A is incorrect because AWS WAF is most suited for prevention against cross-site scripting attacks on AWS infrastructure and services.
Options B is incorrect because AWS WAF is most suited for prevention against SQL Injection attacks on AWS infrastructure and services.
Option C is CORRECT because CloudFront has extensive mitigation techniques for standard flood-type attacks against SSL.
To thwart SSL renegotiation-type attacks, CloudFront disables renegotiation and hence protects against DDoS attacks on AWS infrastructure and services.
Option D is incorrect because for better protection against Malware on AWS, services such as AWS Inspector, EC2 Systems Manager, and AWS Shield can be used.
For more information on security with CloudFront, kindly refer to the following URL:
https://d1.awsstatic.com/whitepapers/Security/Secure_content_delivery_with_CloudFront_whitepaper.pdf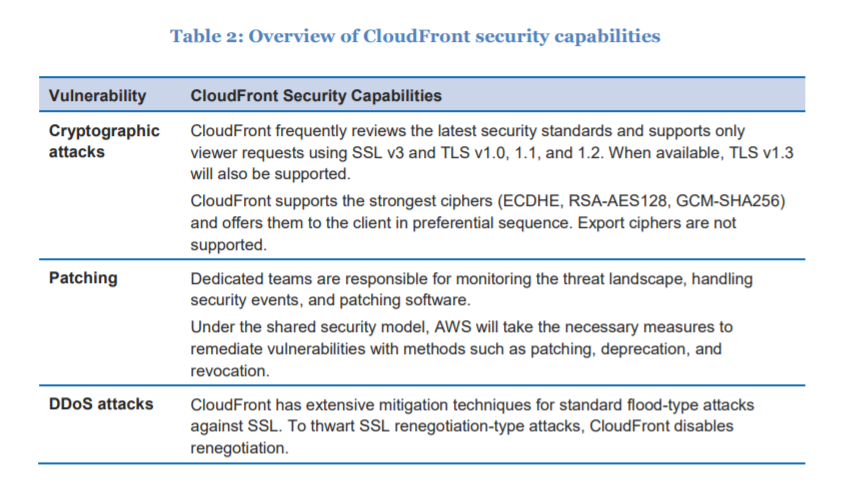
Out of the four options given, AWS CloudFront is most suited for mitigating Distributed Denial of Service (DDoS) attacks.
AWS CloudFront is a content delivery network that can distribute static and dynamic web content, videos, and other files to users all over the world, with low latency and high data transfer speeds. It has several features that make it ideal for mitigating DDoS attacks, including:
DDoS protection: AWS CloudFront can be configured to detect and mitigate DDoS attacks at the edge, closer to the source of the attack. It can handle large-scale volumetric attacks by scaling up automatically, and it can identify and block specific types of attacks, such as SYN floods, UDP floods, and HTTP floods.
Global network of edge locations: AWS CloudFront has a global network of edge locations that can cache and distribute content, which can reduce the load on the origin servers and help prevent DDoS attacks from overwhelming them.
AWS Shield Standard: AWS CloudFront comes with AWS Shield Standard, which provides basic DDoS protection for all AWS customers at no additional cost. It can detect and mitigate most common network and transport layer attacks, such as SYN floods, UDP floods, and reflection attacks.
Cross-site scripting (XSS) and SQL injection are both web application vulnerabilities that allow attackers to execute malicious code on the user's browser or the backend database. AWS CloudFront does not provide specific protections against these types of attacks, but it can help prevent them by caching and serving static content, which can reduce the attack surface of the web application.
Malware attacks are typically executed by infecting user devices with malicious software, such as viruses or trojans. AWS CloudFront does not provide protection against malware attacks, but AWS provides several other services, such as Amazon GuardDuty and Amazon Inspector, which can help detect and mitigate these types of threats.
In summary, AWS CloudFront is most suited for mitigating DDoS attacks, but it can also help prevent other types of attacks by caching and serving static content. However, web application vulnerabilities and malware attacks require additional security measures beyond AWS CloudFront.