Security Requirement for AWS Cognito
Question
You are developing an application that is going to make use of AWS Cognito.
The default sign-in and sign-up features of the AWS Cognito service will be used.
There is a security requirement to ensure that if the user's credentials are compromised, then they would need to use a new password.
Which of the following needs to be in place for this? Choose 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - A and B.
This is given in the AWS Documentation.
Option C is incorrect since this configuration needs to be done in the Advanced Security section.
Option D is incorrect.
Currently, Amazon Cognito doesn't check for compromised credentials for sign-in operations with Secure Remote Password (SRP) flow, which doesn't send the password during sign-in.
For more information on Cognito User pools, please refer to the below URL-
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pool-settings-compromised-credentials.html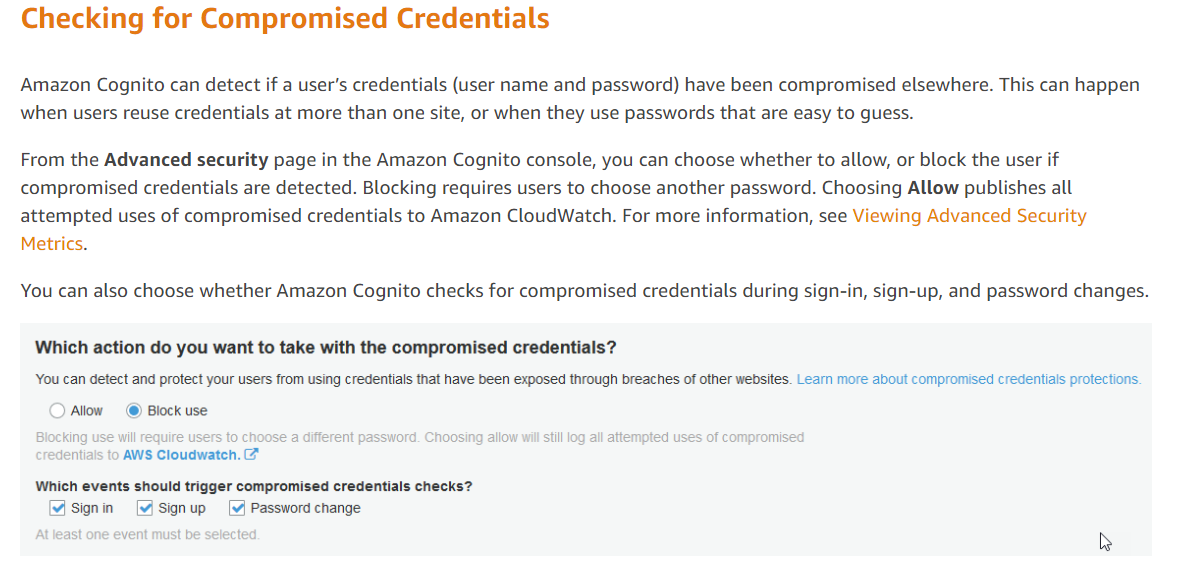
To meet the security requirement of forcing users with compromised credentials to create new passwords, the following two actions need to be taken:
A. Create a User Pool in AWS Cognito: A User Pool is a user directory in AWS Cognito where users can sign up, sign in, and manage their profiles. When a user signs up or signs in, the user pool authenticates the user's credentials and issues JSON web tokens (JWTs) to authorized users. By creating a User Pool, you can enable sign-up and sign-in for users and apply policies such as password strength and expiry rules.
B. Enable "Block use" for compromised credentials in the Advanced Security section: The Advanced Security section in AWS Cognito provides an option to block user accounts in case of any unusual sign-in activity or when a user's credentials are compromised. By enabling this feature, AWS Cognito will monitor user accounts for any unusual activity and automatically block the account if it detects any suspicious behavior.
C. (Incorrect) There is no option for "Block use" for compromised credentials in the Basic Security section. The Basic Security section in AWS Cognito provides a basic level of security for user accounts. It does not provide the option to block user accounts for any unusual activity or when a user's credentials are compromised. Therefore, option C is incorrect.
D. (Incorrect) Verify sign-in operation on Cognito using Secure Remote Password (SRP): Secure Remote Password (SRP) is a cryptographic protocol used for password-based authentication. It is a secure way to protect user credentials from being intercepted during the authentication process. However, this option does not address the requirement of forcing users with compromised credentials to create new passwords. Therefore, option D is incorrect.
In summary, options A and B are correct. To ensure that users with compromised credentials need to use new passwords, create a User Pool in AWS Cognito and enable "Block use" for compromised credentials in the Advanced Security section.