Configure AWS Config Rule Trigger for EC2 Security Groups
Question
You need to configure a new custom AWS Config rule to check whether EC2 security groups in your AWS account are compliant with the company's security policies.
One colleague has already created a Lambda function which you can use to perform the checks of security groups.
For the Config rule, you would need to make sure that whenever there is a configuration change in any EC2 security group, the rule is triggered to evaluate the related security group resources.
How would you specify the trigger of the Config rule?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer : D.
Option A is incorrect because the scope of changes should not be “All changes” otherwise the rule will be triggered whenever any resource recorded by AWS Config is created, changed, or deleted.
Option B is incorrect because the rule is not required to be triggered periodically.
Instead, it should be triggered for the configuration changes of EC2 security groups.
Option C is incorrect because you would need to add the tag for all the security groups if you configure the tag in the scope of changes.
However, you can directly specify security groups in the trigger scope.
Option D is CORRECT because with the settings, the rule is triggered when there is a configuration change for any security group.
The following is an example of the trigger:
Reference:
https://docs.aws.amazon.com/config/latest/developerguide/evaluate-config-rules.html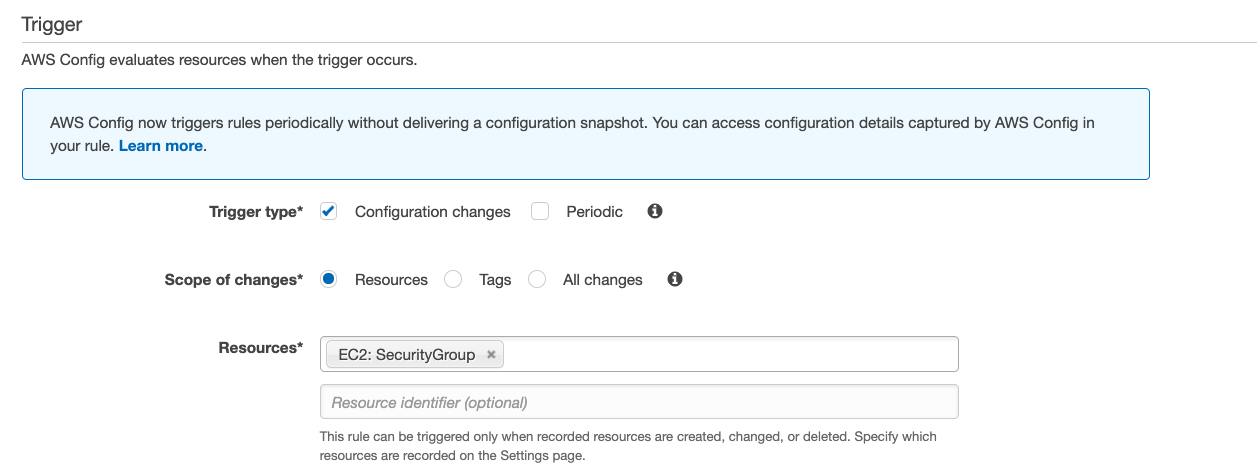
The correct answer is D. In the Config rule trigger, specify the trigger type to be “Configuration changes” and the scope of changes to be “EC2: SecurityGroup”.
Explanation:
AWS Config provides a set of pre-defined rules that can be used to evaluate resources against pre-defined compliance rules. In addition, AWS Config allows users to create custom rules to evaluate resources based on their organization's specific compliance requirements.
In this scenario, we need to create a custom rule to evaluate whether the EC2 security groups in our account are compliant with our organization's security policies.
To create a custom rule, we can use an AWS Lambda function to perform the compliance checks. Whenever there is a configuration change in any EC2 security group, the rule should be triggered to evaluate the related security group resources.
To specify the trigger for the Config rule, we need to select the appropriate trigger type and scope of changes.
Option A: In the Config rule trigger, specify the trigger type to be “Configuration changes” and configure the scope of changes to be “All changes” for all the EC2 resources.
This option is not appropriate because it is too broad. We only want to evaluate the EC2 security groups, not all EC2 resources.
Option B: Add a trigger in the Config rule, select the “Periodic” trigger type with a frequency of 1 hour and choose “EC2: SecurityGroup” in the trigger scope.
This option is not appropriate because it is too infrequent. We want the rule to be triggered whenever there is a configuration change in any EC2 security group, not just every hour.
Option C: Create a trigger with the configuration change type and select the security group tag in the scope of changes. Make sure all existing and new security groups have the tag that you defined.
This option is also not appropriate because it requires tagging every security group with a specific tag. This may be difficult to implement and manage, especially if there are many security groups.
Option D: In the Config rule trigger, specify the trigger type to be “Configuration changes” and the scope of changes to be “EC2: SecurityGroup”.
This is the correct option because it specifies the trigger type as "Configuration changes" and the scope of changes as "EC2: SecurityGroup". This means that the rule will be triggered whenever there is a configuration change in any EC2 security group, which is exactly what we want.
Therefore, the correct answer is D. In the Config rule trigger, specify the trigger type to be “Configuration changes” and the scope of changes to be “EC2: SecurityGroup”.
