Steps to Protect Your Web Application Against DDoS Attacks
Question
A company is deploying a new web application on AWS.
Based on their other web applications, they anticipate being the target of frequent DDoS attacks.
Which steps can the company take to protect its application? Select 2 answers from the options given below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answer: B and D.
Option A is incorrect because during a DDoS attack, a large number of IP addresses may be used, and the Security Group cannot blacklist IPs.
Option B is CORRECT because by doing this we can have the application available to cater to the users during a time of an ongoing DDoS attack.
Option C is incorrect because AWS Inspector cannot be used to examine traffic, hence cannot confirm when a DDOS attack is occurring on the infrastructure.
Option D is CORRECT because AWS WAF is the recommended service to protect against DDoS attacks.
Option E is incorrect because GuardDuty is used as a continuous security monitoring service but does not protect against DDoS attacks on the entire application.
The below diagram from AWS shows how to avoid DDoS attacks using services such as AWS Cloudfront, WAF, ELB and Autoscaling:
For more information on DDoS mitigation from AWS, please visit the below URL:
https://aws.amazon.com/answers/networking/aws-ddos-attack-mitigation/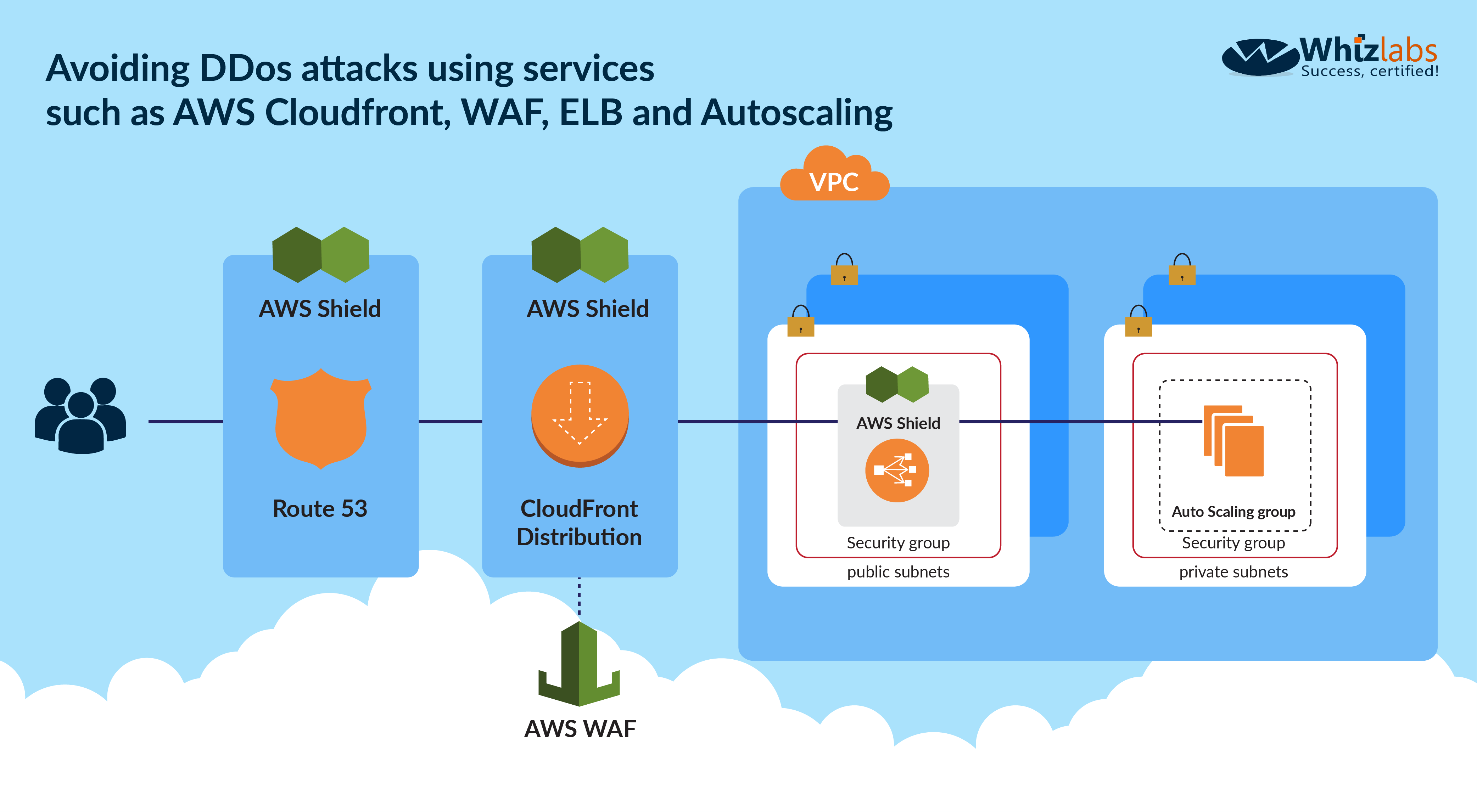
The correct answers are B and D.
Explanation:
A DDoS attack, or Distributed Denial of Service attack, is a type of cyberattack in which an attacker floods a target system or network with traffic to overwhelm its resources and make it unavailable to legitimate users. To protect a web application against DDoS attacks on AWS, the company can take the following steps:
A. Associate the EC2 instances with a security group that blocks traffic from blacklisted IP addresses. This option is not effective against DDoS attacks because the number of IP addresses used in the attack can be very high and constantly changing, making it impractical to maintain an updated list of blacklisted IPs. Additionally, DDoS attacks are typically carried out using botnets, which use compromised devices that have legitimate IP addresses.
B. Use an AWS Application Load Balancer and Auto Scaling group to scale to absorb malicious traffic. This option is effective because it uses an Application Load Balancer (ALB) to distribute traffic across multiple instances, and an Auto Scaling group to automatically add or remove instances based on traffic demand. This allows the application to scale to absorb the malicious traffic generated by a DDoS attack and continue to serve legitimate users.
C. Use Amazon Inspector on the EC2 instances to examine incoming traffic and discard malicious traffic. Amazon Inspector is a service that helps to improve the security and compliance of applications deployed on AWS. However, it is not specifically designed to protect against DDoS attacks, and it may not be effective against large-scale attacks.
D. Use CloudFront and AWS WAF to prevent malicious traffic from reaching the application. This option is effective because it uses AWS Web Application Firewall (WAF) to filter and block malicious traffic before it reaches the application, and Amazon CloudFront to distribute content and absorb the attack traffic. AWS WAF uses customizable rules to block common attack patterns, such as SQL injection and cross-site scripting (XSS), and it can be configured to block traffic from known bad IP addresses or countries.
E. Enable GuardDuty to block malicious traffic from reaching the application. Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior on AWS. However, it is not designed to block traffic or protect against DDoS attacks.
In summary, to protect a web application against DDoS attacks on AWS, the company should use an AWS Application Load Balancer and Auto Scaling group to scale to absorb malicious traffic, and use CloudFront and AWS WAF to prevent malicious traffic from reaching the application.