Detecting Unrestricted Inbound SSH Traffic in AWS Security Groups
Question
You are a DevOps engineer working in a big organization and you manage AWS resources including EC2 and RDS.
One day, the security group of an EC2 bastion host has been modified to allow the inbound SSH traffic from any IP addresses.
You notice this potential security risk after several days.
Although this issue did not lead to any data leakage, you still want to enhance the AWS configurations so that whenever the IP addresses of the incoming SSH traffic in the security groups are not restricted, you will get a notification in time.
Which option is the most suitable?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: A.
Option A is CORRECT because the rule can check if IP addresses of the incoming SSH traffic in the security groups are restricted.
Please check the following screenshot.
Option B is incorrect because this rule checks whether security groups disallow unrestricted incoming TCP traffic to the specified ports.
It is not used only for SSH traffic.
Option A is more suitable than this one.
Option C is incorrect because Amazon Inspector is not able to check the security group configurations with the rule package "Common Vulnerabilities and Exposures-1.1"
The rule package "Network Reachability-1.1" should be chosen.
Besides, Amazon Inspector normally takes a longer time to scan so it may not provide a timely notification.
Option D is incorrect because Amazon GuardDuty is a continuous security monitoring service to identify unexpected and potentially unauthorized and malicious activity within your AWS environment.
It cannot provide a notification when a security group has been changed.
Reference:
https://docs.aws.amazon.com/config/latest/developerguide/restricted-ssh.html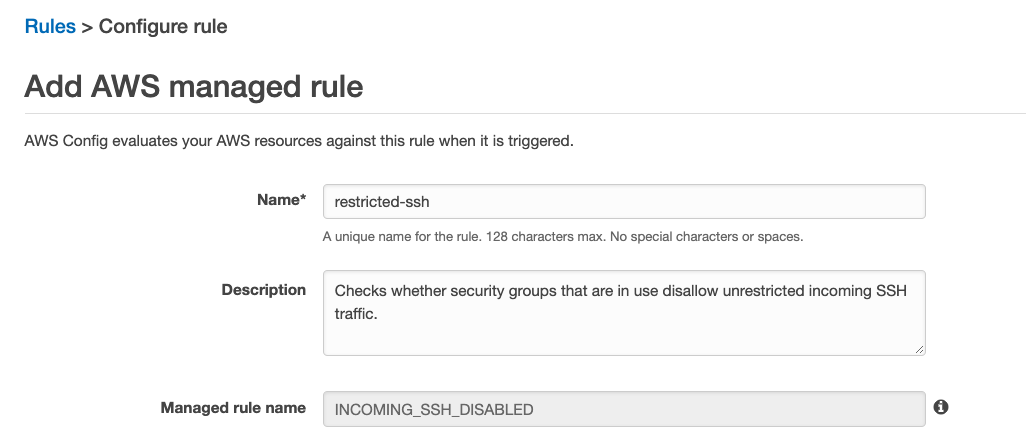
The best option for enhancing AWS configurations to receive notifications whenever incoming SSH traffic to security groups is not restricted is to create an AWS Config rule and select the AWS Managed rule "restricted-ssh" (option A).
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. It provides a detailed inventory of your resources and their configurations, along with configuration history and change tracking. AWS Config rules allow you to define desired configurations and detect when they are not met, triggering notifications or taking corrective actions.
The "restricted-ssh" AWS Managed rule is designed to check whether security groups disallow unrestricted incoming SSH traffic. This rule will evaluate all security groups associated with EC2 instances in your AWS account and identify those that have inbound rules allowing SSH traffic from any IP address (0.0.0.0/0). If such a rule is found, the rule will be evaluated as non-compliant, and you can configure AWS Config to notify you of this event through Amazon SNS.
Option B, adding a rule in AWS Config and selecting the AWS Managed rule "restricted-common-ports", is not as suitable because this rule is designed to check whether security groups allow unrestricted access to commonly exploited ports, not specifically SSH traffic.
Option C, enabling Amazon Inspector and including the rule package "Common Vulnerabilities and Exposures-1.1" to check the security groups and configuring a notification through SNS, is not as suitable because this option is designed to detect vulnerabilities in your instances and their associated resources, not specifically the security groups.
Option D, enabling Amazon GuardDuty and checking the security findings of security groups in AWS Security Hub, is also not as suitable because this option is designed to monitor and detect malicious activity and unauthorized behavior in your AWS account, not specifically the security groups.
In summary, option A, creating an AWS Config rule and selecting the AWS Managed rule "restricted-ssh", is the most suitable option for enhancing AWS configurations to receive notifications whenever incoming SSH traffic to security groups is not restricted.
