The Best Way to Allow Mobile App Users Access to AWS Resources
Question
I have a Mobile App that needs to access AWS resources like S3, DynamoDB.
What is the best way to allow users of the mobile app access to these AWS resources?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer: B.
A mobile app that becomes popular can have a large user base.
The best way to provide access to AWS resources in this scenario will be to use Federated Identity access using External Identity Providers(IdP) like Amazon, Facebook, Google etc.
The mobile app can establish trust with these well-known IdPs and take advantage of the authentication mechanisms to validate user identity.
As shown in the figure below, the mobile app uses Amazon as the external IdP for accepting user credentials & authenticating him.
Using Cognito & the Security Token Service, the Mobile App then gets temporary Security Credentials for accessing the AWS resources required by the app.
The role associated with the STS token and its assigned policies determine what can be accessed.
Option A is incorrect.
Distributing long-term AWS Security Credentials with external applications is not recommended since the credentials may be compromised resulting in security breaches.
Option B is CORRECT.
The STS token will contain temporary credentials with a Role indicating the access level that a mobile app user can have.
The security credentials will be valid for a specific user session only.
Option C is incorrect.
Creating an ever-growing set of Users within AWS IAM and assigning them permissions for accessing AWS resources will be impractical.
Option D is incorrect.
Although it is a viable option to connect to an EC2 instance running a similar web application, it will duplicate effort on the developer's part.
References:
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_oidc_cognito.html https://www.testpreptraining.com/tutorial/aws-cloud-practitioner/aws-access-management/ https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.html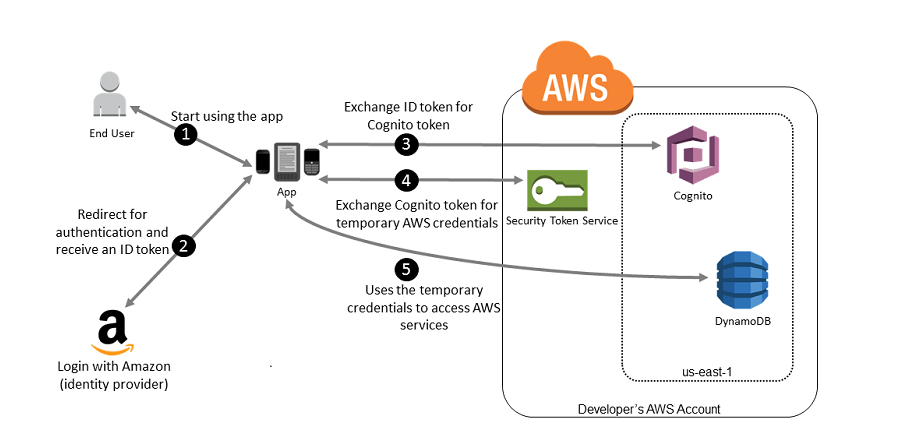
The best way to allow users of a mobile app to access AWS resources such as S3 and DynamoDB depends on several factors, such as security, scalability, and ease of management. However, there are several ways to accomplish this task.
A. Keeping the Security Credentials within the Mobile App This option is not recommended as it poses a significant security risk. If the security credentials, such as AWS access keys or IAM user credentials, are stored in the mobile app, they can be easily compromised by malicious attackers. Once attackers gain access to the credentials, they can use them to access sensitive data or resources.
B. Using Security Token Service (STS) with Identity Federation This option provides a more secure way of accessing AWS resources. STS is a web service that provides temporary security credentials for accessing AWS resources. Identity federation allows users to access AWS resources using their existing identity and credentials, such as Facebook, Google, or Amazon accounts.
By using STS with identity federation, the mobile app can obtain temporary security credentials that allow it to access the desired AWS resources within a session. Once the session expires, the credentials are automatically revoked, providing an additional layer of security. This option also simplifies management, as the app developer does not need to create and manage AWS credentials for each user.
C. Creating Users & Groups within IAM This option involves creating IAM users and groups, assigning IAM policies to the users or groups, and providing the necessary credentials to the mobile app. While this option provides fine-grained access control, it can be challenging to manage, especially for a large number of users. Additionally, this option requires the app developer to create and manage AWS credentials for each user, which can be a time-consuming task.
D. Connecting the Mobile App to another Web Application running on EC2 This option involves creating a web application that runs on an EC2 instance and assumes an IAM role for accessing the desired AWS resources. The mobile app can then connect to the web application and request the necessary data or resources. This option provides a secure way of accessing AWS resources, as the mobile app does not store any credentials. However, this option can be challenging to implement, especially for complex applications, and requires additional infrastructure and management overhead.
In summary, the best way to allow users of a mobile app to access AWS resources such as S3 and DynamoDB is by using Security Token Service (STS) with identity federation. This option provides a secure and scalable way of accessing AWS resources, simplifies management, and eliminates the need for app developers to create and manage AWS credentials for each user.