Identifying Potential Services for CloudWatch Event Rule: Service-Last-Accessed Information
Question
In a large corporation, an AWS organization is established with several OUs (organizational units)
Because of several new security requirements, the security operator needs to create several CloudWatch Events rules.
For one rule, the requirement is that if certain AWS services have not been used by an OU for 6 months but are suddenly used recently, an SNS notification will be triggered.
How would you quickly get the service-last-accessed information to identify the potential services to add to the CloudWatch Event rule?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer - D.
The service-last-accessed information can be viewed in the IAM access advisor.
Check the introduction in.
https://aws.amazon.com/blogs/security/set-permission-guardrails-using-iam-access-advisor-analyze-service-last-accessed-information-aws-organization/.Option A is incorrect: Because there is no such information in the AWS Organization console.
Option B is incorrect: Because the AWS Config service does not provide such information.
Instead, the user can use AWS CLI to call the IAM access advisor endpoint to get the data.
Option C is incorrect AWS Resource Groups can query and group resources.
However, it does not provide the data required in this case.
Option D is CORRECT: Because the service-last-accessed information for each OU can be found in the IAM access advisor.
Take the below snapshot as an example:
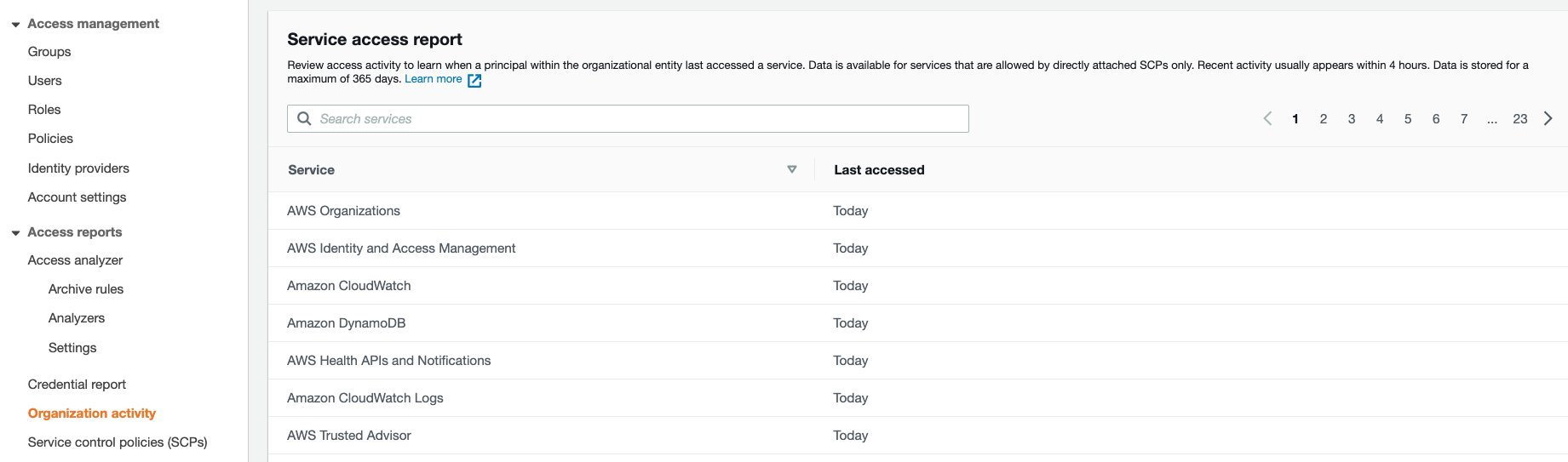
To quickly get the service-last-accessed information to identify potential services to add to the CloudWatch Event rule, the best option is to use the IAM access advisor.
Option D is the correct answer. The IAM access advisor provides the last accessed information for AWS services and actions within the AWS account. It allows you to review the services and actions that each IAM user, role, or group has accessed in the last 180 days. It also provides the number of times each service or action has been accessed, and when it was last accessed.
By reviewing the IAM access advisor information for each OU, you can determine which services have not been used in the last six months, but have been used recently, and should be added to the CloudWatch Event rule.
Option A is not a practical solution for large organizations, as it would require clicking on each OU and reviewing the service-last-accessed information individually.
Option B is not correct because the AWS Config service does not provide service-last-accessed information. It provides configuration data for AWS resources, including the current and previous configuration states of each resource.
Option C is also not a suitable solution because the AWS Resource Groups service allows you to group resources based on tags, resource types, or other criteria, but it does not provide service-last-accessed information.