Access Denied Error
Question
Your organization AWS Setup has an AWS S3 bucket which stores confidential documents which can be only downloaded by users authenticated and authorized via your application.
You do not want to create IAM users for each of these users and as a best practice you have decided to generate AWS STS Federated User temporary credentials each time when a download request is made and then use the credentials to generate presigned URL and redirect user for download.
However, when user is trying to access the presigned URL, they are getting Access Denied Error.
What could be the reason?
Answers
Explanations
Click on the arrows to vote for the correct answer
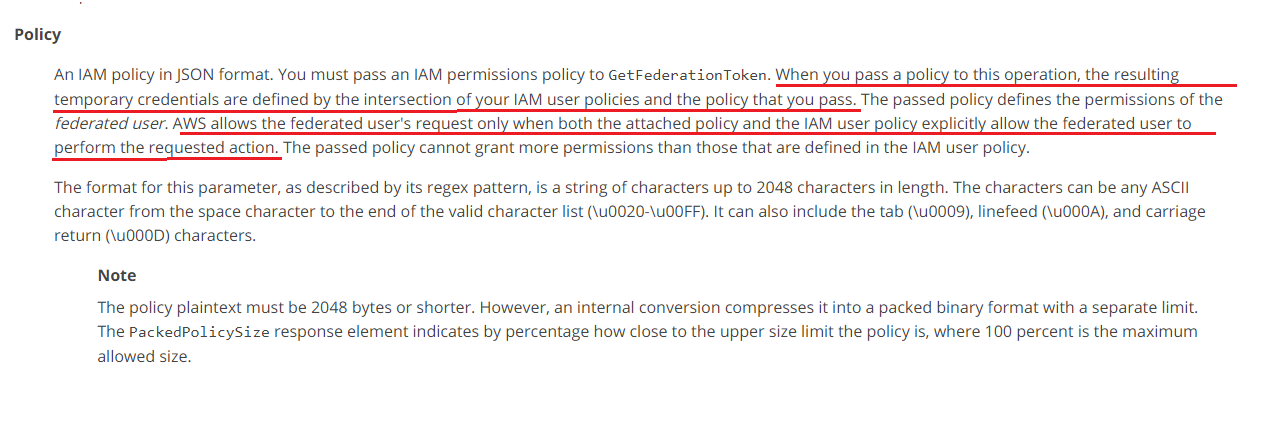
A. B. C. D.Answer: B.
Option A is not a correct statement.
Option B is correct.
https://docs.aws.amazon.com/STS/latest/APIReference/API_GetFederationToken.htmlOption C is not correct.
You can generated FederatedUser credentials using an IAM User, not using an IAM Role.
Option D is not a correct statement.
The most likely reason for the Access Denied Error is option C: IAM Role used to generate Federated User credentials does not have access on S3 bucket.
When generating temporary security credentials using AWS Security Token Service (STS), you need to specify an IAM role that defines the permissions for the federated user. This IAM role must have the necessary permissions to access the S3 bucket that stores the confidential documents.
Here are some steps to check if the IAM role has access to the S3 bucket:
Go to the IAM console and select the IAM role that is used to generate the temporary security credentials.
Check if the IAM role has a policy that allows access to the S3 bucket. The policy should have an action that grants access to the S3 bucket, such as "s3:GetObject", "s3:PutObject", or "s3:ListBucket".
If the IAM role doesn't have a policy that grants access to the S3 bucket, you need to create a new policy or modify the existing policy to include the necessary permissions.
After creating or modifying the policy, attach it to the IAM role.
Test the presigned URL again to see if the Access Denied Error has been resolved.
Option A (AWS STS service must be given access in S3 bucket ACL) is not correct because the ACL (Access Control List) of the S3 bucket only controls access to the bucket itself, not to the AWS STS service.
Option B (IAM User used to generate Federated User credentials does not have access on S3 bucket) is not correct because IAM users are not used to generate temporary security credentials for federated users. IAM users are used to manage access to AWS resources, but they are not suitable for granting access to external users.
Option D (Your application must be whitelisted in AWS STS service to perform FederatedUser action) is not correct because there is no requirement to whitelist an application in the AWS STS service. However, you do need to make sure that the application is configured to use the temporary security credentials generated by the AWS STS service.