Configure AWS Security Hub for CIS AWS Foundations Benchmark and PCI DSS Compliance
Question
You need to configure AWS Security Hub to provide a comprehensive view of the security state in AWS and to check AWS Organizations against industry-based security standards.
Security Hub should include the security standards of CIS AWS Foundations Benchmark and PCI DSS.
Which of the following actions must be done before enabling AWS Security Hub?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Correct Answer: D.
Option A is incorrect because enabling Trusted Advisor is not a prerequisite for AWS Security Hub.
The Trusted Advisor data is not sent to the Security Hub.
Option B is incorrect because you do not need to create any CloudFormation StackSet to enable Security Hub.
Option C is incorrect because the SNS topic is not required for enabling Security Hub.
Option D is CORRECT because before enabling Security Hub, you must first enable resource recording in AWS Config:
Security Hub uses Service-linked AWS Config rules to perform most of its security checks for controls.
Reference:
https://docs.aws.amazon.com/securityhub/latest/userguide/securityhub-prereq-config.html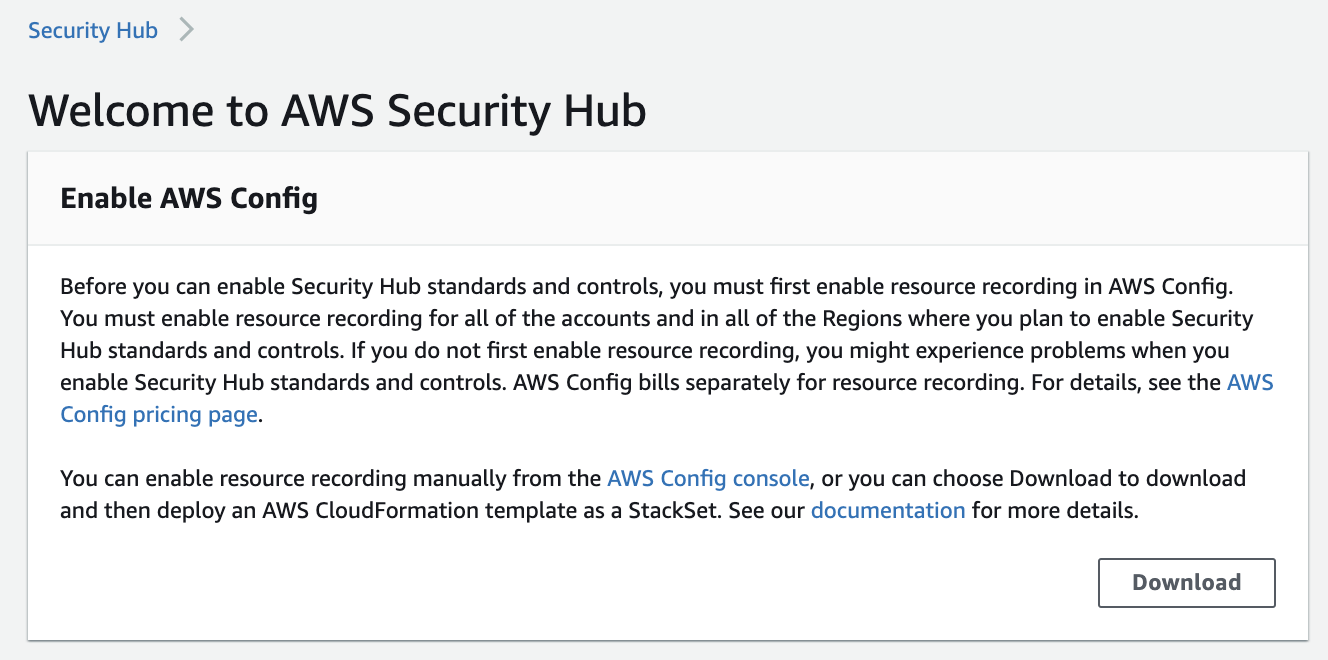
To enable AWS Security Hub and to provide a comprehensive view of the security state in AWS, and check AWS Organizations against industry-based security standards like CIS AWS Foundations Benchmark and PCI DSS, we need to perform the following actions:
Step 1: Enable AWS Security Hub To enable AWS Security Hub, we need to navigate to the AWS Security Hub console and click on "Enable Security Hub." This step creates an AWS Security Hub account that is automatically integrated with other AWS services.
Step 2: Enable AWS Config in all AWS accounts of the AWS Organization AWS Config is a service that enables us to assess, audit, and evaluate the configuration of our AWS resources. By enabling AWS Config, we can track changes made to our resources and their compliance with the defined policies. This step is essential because AWS Security Hub relies on AWS Config to collect data about our resources and to provide a comprehensive view of our security state. We need to enable AWS Config in all AWS accounts of the AWS Organization in the region where Security Hub is enabled.
Step 3: Configure AWS Security Hub Standards To check AWS Organizations against industry-based security standards, we need to configure AWS Security Hub Standards. AWS Security Hub currently supports the following standards:
- AWS Foundational Security Best Practices standard
- CIS AWS Foundations Benchmark standard
- PCI DSS standard
In this case, we need to enable the CIS AWS Foundations Benchmark and the PCI DSS standards. This step is important because it allows AWS Security Hub to continuously check our accounts and workloads against these security standards and provide us with a comprehensive view of our security state.
Step 4: Add AWS accounts to AWS Security Hub After enabling AWS Security Hub and AWS Config, we need to add AWS accounts to Security Hub to include the security checks of AWS accounts and workloads. We can add accounts manually, or we can use AWS Organizations to automate this process. We can enable AWS Security Hub in all AWS accounts of the AWS Organization by creating a CloudFormation StackSet and adding the IAM service account in all AWS accounts of the AWS Organization.
Step 5: Configure SNS Topic for Security Hub Notifications To receive notifications of security findings in AWS Security Hub, we need to configure an SNS topic. We can configure an SNS topic for all AWS accounts of the AWS Organization to perform notifications of security findings in AWS Security Hub.
Based on the above steps, the correct answer is option D - "Enable AWS Config on all accounts of the AWS Organization in the Region where Security Hub is enabled." Option A is incorrect because Trusted Advisor is not a prerequisite for enabling AWS Security Hub. Option B is incorrect because creating a CloudFormation StackSet is just one step in adding AWS accounts to Security Hub. Option C is incorrect because we do not need to configure an SNS topic before enabling AWS Security Hub, but we can configure it after adding AWS accounts to Security Hub.