Approaches for Authenticating and Accessing S3 in an AWS VPC
Question
A corporate web application is deployed within an Amazon Virtual Private Cloud (VPC) and is connected to the corporate data center via an IPsec VPN.
The application must authenticate against the on-premises LDAP server.
After authentication, each logged-in user can only access an Amazon Simple Storage Service(S3) keyspace specific to that user.
Which two approaches can satisfy these objectives?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B and C.
There are two architectural considerations here: (1) The users must be authenticated via the on-premise LDAP server, and (2) each user should have access to S3 only.
With this information, it is important to authenticate the users using LDAP, get the IAM Role name, get the temporary credentials from AWS STS, and access the S3 bucket using those credentials.
And second, create an IAM Role that provides access to S3.
Option A is incorrect because the users need to be authenticated using LDAP first, not AWS STS.
Also, the temporary credentials to log into AWS are provided by AWS STS, not an identity broker.
Option B is CORRECT because it follows the correct sequence.
It authenticates users using LDAP, gets the security token from AWS STS, and then accesses the S3 bucket using the temporary credentials.
Option C is CORRECT because it follows the correct sequence.
It develops an identity broker that authenticates users against LDAP, gets the security token from AWS STS, and then accesses the S3 bucket using the IAM federated user credentials.
Option D is incorrect because you cannot use the LDAP credentials to log in to IAM.
An example diagram of how this works from the AWS documentation is given below.
For more information on federated access, please visit the below link-
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios_federated-users.html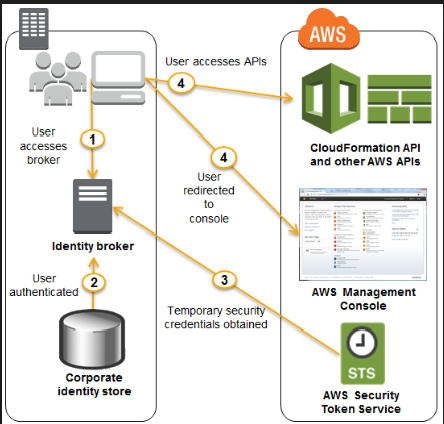
The scenario presented involves a corporate web application that is deployed within an Amazon Virtual Private Cloud (VPC) and is connected to the corporate data center via an IPsec VPN. The application must authenticate against the on-premises LDAP server, and each logged-in user can only access an Amazon S3 keyspace specific to that user. Two approaches can satisfy these objectives:
A. Develop an identity broker that authenticates against AWS Security Token Service (STS) to assume an IAM role to get temporary AWS security credentials. The application calls the identity broker to get AWS temporary security credentials to access the appropriate S3 bucket.
This approach involves developing an identity broker that authenticates against AWS Security Token Service (STS) to assume an IAM role to obtain temporary AWS security credentials. The application then calls the identity broker to obtain the temporary credentials required to access the appropriate S3 bucket.
In this approach, the identity broker authenticates against AWS Security Token Service (STS) by assuming an IAM role. The IAM role is configured with the necessary permissions to access the appropriate S3 bucket. Once the identity broker has assumed the IAM role, it obtains temporary AWS security credentials from STS. These temporary credentials are then passed to the application, which uses them to access the appropriate S3 bucket.
B. The application authenticates against LDAP and retrieves the name of an IAM role associated with the user. The application then calls the AWS Security Token Service (STS) to assume that IAM role ( including the ARN ). The application then uses the temporary credentials to access the appropriate S3 bucket.
This approach involves the application authenticating against LDAP and retrieving the name of an IAM role associated with the user. The application then calls the AWS Security Token Service (STS) to assume that IAM role, including the ARN. The application then uses the temporary credentials obtained from STS to access the appropriate S3 bucket.
In this approach, the application authenticates against LDAP and retrieves the name of the IAM role associated with the user. The application then calls STS to assume that IAM role, which is configured with the necessary permissions to access the appropriate S3 bucket. The application then uses the temporary credentials obtained from STS to access the S3 bucket.
C. Develop an identity broker that authenticates against LDAP and then calls AWS Security Token Service (STS) to get IAM federated user credentials. The application then uses the temporary credentials to access the appropriate S3 bucket.
This approach involves developing an identity broker that authenticates against LDAP and then calls AWS Security Token Service (STS) to obtain IAM federated user credentials. The application then uses the temporary credentials obtained from STS to access the appropriate S3 bucket.
In this approach, the identity broker authenticates against LDAP and obtains IAM federated user credentials from STS. These temporary credentials are then passed to the application, which uses them to access the appropriate S3 bucket.
D. The application authenticates against LDAP and then calls the AWS Identity and Access Management (IAM) Security service to log in to IAM using the LDAP credentials. The application can then access the appropriate S3 bucket.
This approach involves the application authenticating against LDAP and then calling the AWS Identity and Access Management (IAM) Security service to log in to IAM using the LDAP credentials. The application can then access the appropriate S3 bucket.
In this approach, the application authenticates against LDAP and uses the LDAP credentials to log in to IAM. Once logged in, the application can access the appropriate S3 bucket.
In summary, options A and B are both viable solutions to the given scenario. Option A involves developing an identity broker that authenticates against AWS STS to assume an IAM role and obtain temporary AWS security credentials, while option B involves the application authenticating against LDAP and retrieving the name of an IAM role associated with