Reduce VPN Connections for Seamless Communication Between AWS VPCs and On-Premise Services
Question
A company currently has a number of VPC's hosted in AWS.
They also have a VPN connection between their on-premise data center and AWS.
They want to limit the number of VPN connections they would need to create in order to ensure that the VPC's hosted in AWS can talk to the on-premise services.
Which of the below is a way that this can be achieved.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.Answer - B.
The AWS documentation mentions the following.
For more information on VPC-VPN connection sharing , please refer to the below link.
https://aws.amazon.com/answers/networking/aws-multiple-vpc-vpn-connection-sharing/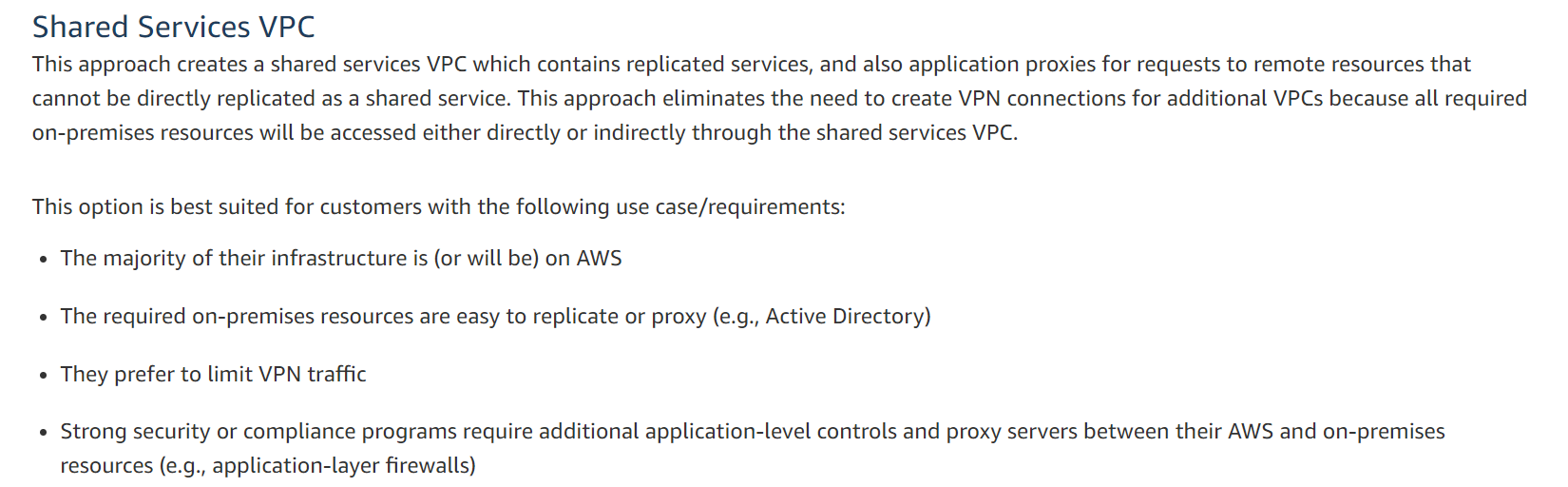
The company wants to limit the number of VPN connections they need to create in order to ensure that the VPC's hosted in AWS can talk to the on-premise services. There are several ways to achieve this goal:
A. Peer the VPC's together and then forward the traffic through one of the VPC's: This method involves peering all the VPCs together and then forwarding the traffic through one of the VPCs. This way, only one VPN connection is needed between the on-premise data center and the VPC that is used as a hub for all the other VPCs. However, this method requires all the VPCs to be peered together, which may not be desirable in all cases.
B. Create a shared services VPC and route all requests to the other VPCs via this VPC: This method involves creating a shared services VPC and routing all requests from the other VPCs through this VPC. This way, only one VPN connection is needed between the on-premise data center and the shared services VPC. The shared services VPC can be used to host services that are commonly used by all the other VPCs, such as DNS or authentication services.
C. There is no way, you need to ensure there is a VPN connection between each VPC and the on-premise infrastructure: This answer is incorrect. There are ways to limit the number of VPN connections needed between the on-premise data center and the VPCs hosted in AWS, as described above.
D. Make use of an AWS Storage Gateway to integrate AWS Cloud with existing on-premise infrastructure: This method involves using an AWS Storage Gateway to integrate AWS Cloud with existing on-premise infrastructure. This can be useful for integrating storage services, such as Amazon S3, with on-premise applications. However, it may not be suitable for all types of services that need to communicate between the on-premise data center and the VPCs hosted in AWS.
In conclusion, the best option to limit the number of VPN connections needed between the on-premise data center and the VPCs hosted in AWS is to create a shared services VPC and route all requests to the other VPCs via this VPC. This approach provides a centralized hub for all traffic and allows for the creation of a shared infrastructure that can be used by all VPCs.
