Allow HTTPS over TCP Port 443 to Web01 and Prevent HTTP over TCP Port 80
Question
SIMULATION -
Overview -
The following section of the exam is a lab. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
To start the lab -
You may start the lab by clicking the Next button.
You plan to host several secured websites on Web01.
You need to allow HTTPS over TCP port 443 to Web01 and to prevent HTTP over TCP port 80 to Web01.
What should you do from the Azure portal?
Explanations
See explanation below.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
Step A: Create a network security group
A1. Search for and select the resource group for the VM, choose Add, then search for and select Network security group.
A2. Select Create.
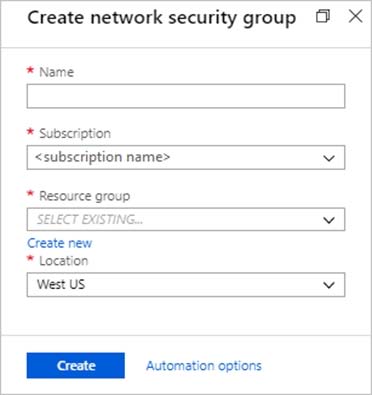
The Create network security group window opens.
A3. Create a network security group
Enter a name for your network security group.
Select or create a resource group, then select a location.
A4. Select Create to create the network security group.
Step B: Create an inbound security rule to allows HTTPS over TCP port 443
B1. Select your new network security group.
B2. Select Inbound security rules, then select Add.
B3. Add inbound rule -
B4. Select Advanced.
From the drop-down menu, select HTTPS.
You can also verify by clicking Custom and selecting TCP port, and 443.
B5. Select Add to create the rule.
Repeat step B2-B5 to deny TCP port 80
B6. Select Inbound security rules, then select Add.
B7. Add inbound rule -
B8. Select Advanced.
Clicking Custom and selecting TCP port, and 80.
B9. Select Deny.
Step C: Associate your network security group with a subnet
Your final step is to associate your network security group with a subnet or a specific network interface.
C1. In the Search resources, services, and docs box at the top of the portal, begin typing Web01. When the Web01 VM appears in the search results, select it.
C2. Under SETTINGS, select Networking. Select Configure the application security groups, select the Security Group you created in Step A, and then select Save, as shown in the following picture:
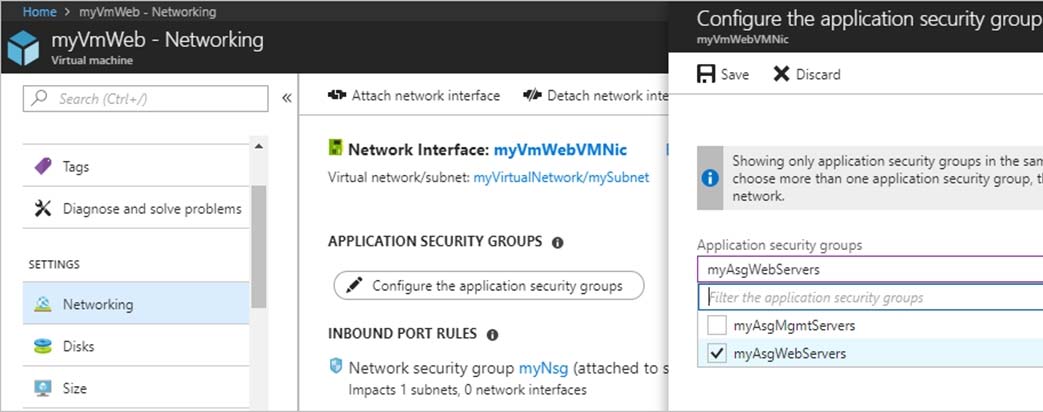
To allow HTTPS over TCP port 443 to Web01 and prevent HTTP over TCP port 80 to Web01, you can perform the following steps from the Azure portal:
Navigate to the Azure portal and select the virtual machine that hosts Web01.
From the left-hand menu, select Networking.
Under the Networking tab, click on the Add inbound port rule button.
In the Add inbound security rule blade, set the following values:
- Name: HTTPS
- Protocol: TCP
- Port range: 443
- Action: Allow
- Priority: 100
- Source: Any
- Destination: VirtualMachine
Click on the Add inbound security rule button to create the rule.
To prevent HTTP over TCP port 80 to Web01, select the existing inbound port rule for HTTP.
Click on the Delete button to remove the existing inbound security rule.
Confirm the deletion by clicking on Yes in the confirmation dialog box.
By performing these steps, you have allowed HTTPS over TCP port 443 to Web01 and prevented HTTP over TCP port 80 to Web01.