Enforcing Multi-Factor Authentication for Global Administrators
Question
You have an Azure Active Directory (Azure AD) tenant.
You have an existing Azure AD conditional access policy named Policy1. Policy1 enforces the use of Azure AD-joined devices when members of the Global
Administrators group authenticate to Azure AD from untrusted locations.
You need to ensure that members of the Global Administrators group will also be forced to use multi-factor authentication when authenticating from untrusted locations.
What should you do?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.D
There are two types of controls:
-> Grant controls "" To gate access
-> Session controls "" To restrict access to a session
Grant controls oversee whether a user can complete authentication and reach the resource that they're attempting to sign-in to. If you have multiple controls selected, you can configure whether all of them are required when your policy is processed. The current implementation of Azure Active Directory enables you to set the following grant control requirements:
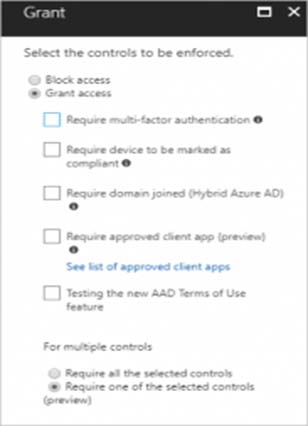
To ensure that members of the Global Administrators group are forced to use multi-factor authentication (MFA) when authenticating from untrusted locations in Azure AD, we need to modify the existing conditional access policy (Policy1) in Azure AD.
Option A - From the Azure portal, modify session control of Policy1 - This option is not correct, as session control settings for a conditional access policy only specify the maximum allowed session duration and the idle time before a user is prompted to re-authenticate. It does not enable or enforce MFA.
Option B - From the multi-factor authentication page, modify the service settings - This option is not correct, as modifying the service settings for MFA applies the settings to all users in the tenant, not just the members of the Global Administrators group.
Option C - From the multi-factor authentication page, modify the user settings - This option is not correct, as modifying the user settings for MFA applies the settings to individual users, not just the members of the Global Administrators group.
Option D - From the Azure portal, modify grant control of Policy1 - This option is also not correct, as grant control specifies which users or groups the policy applies to, but does not enable or enforce MFA.
Therefore, the correct option is to modify the access controls for the existing conditional access policy (Policy1) to include MFA enforcement for members of the Global Administrators group when they authenticate from untrusted locations. To do this, we can follow these steps:
- Sign in to the Azure portal as a Global Administrator.
- Navigate to Azure Active Directory > Conditional Access.
- Find and select the Policy1 policy.
- Click the Edit button to modify the policy.
- Under the "Assignments" section, ensure that the "Users and groups" option is selected.
- Click the "Add user or group" button and select the Global Administrators group.
- Under the "Access controls" section, click the "Grant" tab.
- Click the "Grant access" dropdown menu and select the "Require multi-factor authentication" option.
- Click the "Save" button to save the changes to the policy.
This will modify the Policy1 conditional access policy to enforce MFA for members of the Global Administrators group when they authenticate from untrusted locations.