Provide Specific User Accounts Read Access to Azure Cosmos DB Databases
Question
You have an Azure Active Directory (Azure AD) tenant.
You plan to deploy Azure Cosmos DB databases that will use the SQL API.
You need to recommend a solution to provide specific Azure AD user accounts with read access to the Cosmos DB databases.
What should you include in the recommendation?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.C
The Access control (IAM) pane in the Azure portal is used to configure role-based access control on Azure Cosmos resources. The roles are applied to users, groups, service principals, and managed identities in Active Directory. You can use built-in roles or custom roles for individuals and groups. The following screenshot shows Active Directory integration (RBAC) using access control (IAM) in the Azure portal:
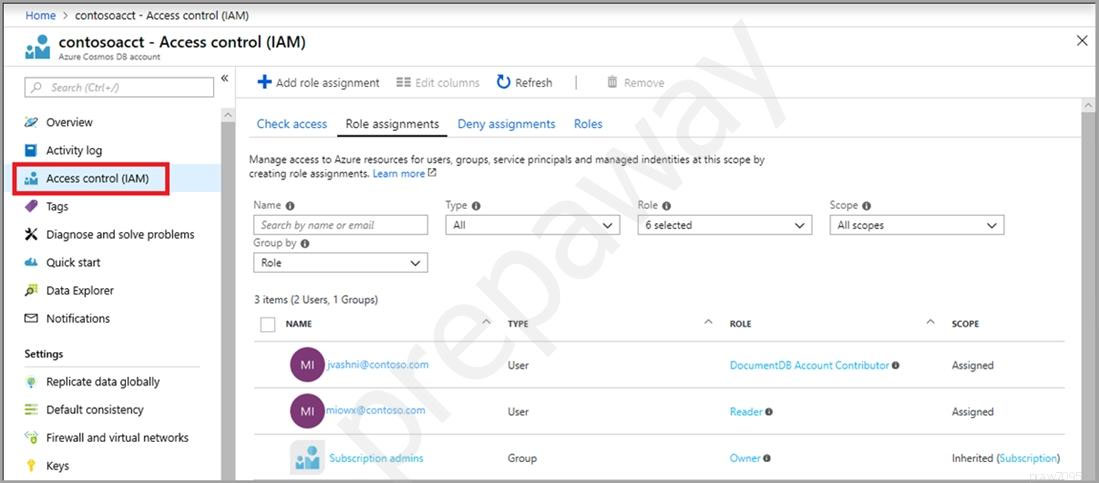
The correct answer is C. a resource token and an Access control (IAM) role assignment.
Explanation: To provide specific Azure AD user accounts with read access to Azure Cosmos DB databases that use the SQL API, we can use Resource tokens and Azure AD-based role assignments. Resource tokens provide time-bound and limited access to specific resources in Cosmos DB. Azure AD-based role assignments provide role-based access control to Azure resources.
To implement this solution, follow these steps:
- Create an Azure AD group and add the users who require access to the group.
- In Azure Cosmos DB, create a new User-Defined Function (UDF) and add the following code to generate the resource token:
javascriptfunction generateToken(resource, operation, expiryUtc) { var crypto = require("crypto"); var key = Buffer.from("<your account master key>", "base64"); var text = (resource || "") + "\n" + (operation || "") + "\n" + (expiryUtc || "") + "\n" + "" + "\n"; var signature = crypto.createHmac("sha256", key).update(text).digest("base64"); var token = encodeURIComponent("type=master&ver=1.0&sig=" + signature); return token; } - In the same UDF, add the following code to retrieve the user's Azure AD object ID:
kotlinfunction getUserId() { var context = getContext(); var user = context.getUser(); if (user == null) { return null; } var userId = user.userId; if (userId == null) { return null; } var parts = userId.split("@"); if (parts.length == 2 && parts[1].toLowerCase() == "<your AAD domain>") { return parts[0]; } return null; } - In the same UDF, add the following code to generate the resource token for the user:
javascriptfunction getUserToken(resource, operation, expiryUtc) { var userId = getUserId(); if (userId == null) { return null; } var token = generateToken(resource, operation, expiryUtc); return encodeURIComponent("type=resource&ver=1.0&uid=" + userId + "&sig=" + token); } - In Azure Cosmos DB, create a new Stored Procedure and add the following code to check if the user has the required role:
javascriptfunction isUserInRole(roleName) { var user = getContext().getUser(); if (user != null && user.roles != null) { for (var i = 0; i < user.roles.length; i++) { var role = user.roles[i]; if (role.toLowerCase() == roleName.toLowerCase()) { return true; } } } return false; } - In the same Stored Procedure, add the following code to generate the resource token for the user and return it:
javascriptfunction getResourceToken(resourceId, permission) { if (!isUserInRole("<your required role>")) { throw new Error("Unauthorized"); } var expiryUtc = "<your expiry time>"; var resourceToken = getUserToken(resourceId, permission, expiryUtc); return resourceToken; } - In your application code, pass the resource token generated by the Stored Procedure to Cosmos DB.
Finally, create an Azure AD-based role assignment that assigns the "Cosmos DB Reader" role to the Azure AD group you created earlier. This role assignment grants read-only access to Cosmos DB databases that use the SQL API.
Therefore, the correct answer is C. a resource token and an Access control (IAM
