Stealth Scan Against Non-Pingable System
Question
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.C.
https://www.freecodecamp.org/news/what-is-nmap-and-how-to-use-it-a-tutorial-for-the-greatest-scanning-tool-of-all-time/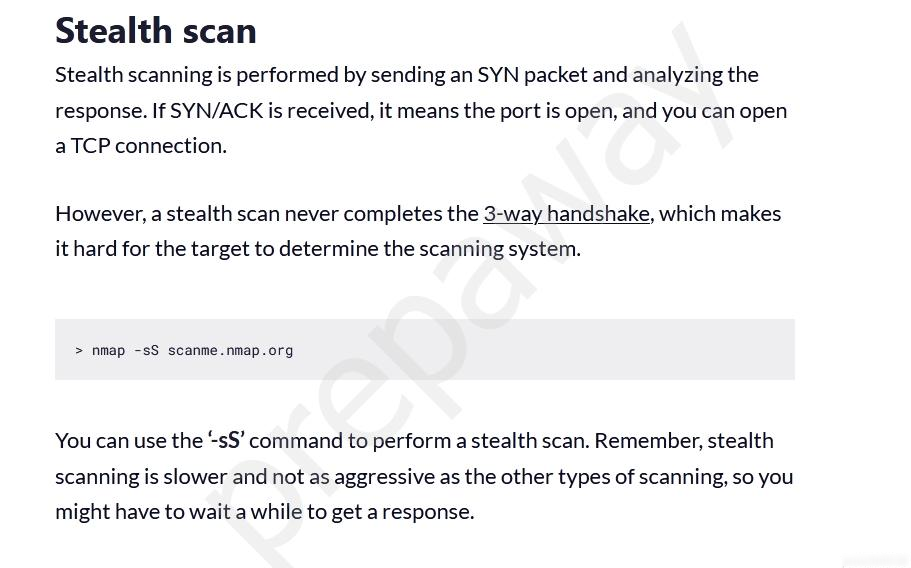
When attempting to do a stealth scan against a system that does not respond to ping, the BEST Nmap command that can be used to accomplish that goal is option C: nmap "sS "O <system> -P0.
Explanation:
Nmap is a powerful and widely used network exploration tool that can be used for various tasks like port scanning, OS detection, and vulnerability assessment. One of the scanning techniques that can be used with Nmap is stealth scanning, which attempts to avoid detection by minimizing the amount of traffic sent to the target system. This can be useful in situations where the network administrator has implemented intrusion detection and prevention systems that are designed to detect and block scanning attempts.
In this scenario, the target system is not responding to ping requests, which means that it is likely configured to ignore ICMP packets. Therefore, using the -noping option in any of the commands is unnecessary as the target is not responding to ping anyway.
Option A (nmap "sA "O <system> -noping) uses the ACK scanning technique, which sends packets with the ACK flag set and expects to receive a RST response if the port is closed. This technique is not effective against systems that have implemented stateful packet inspection, which is common in modern firewalls.
Option B (nmap "sT "O <system> -P0) uses the TCP connect scan technique, which attempts to connect to each port on the target system using a full TCP handshake. This technique can be detected by IDS/IPS systems as it generates a significant amount of traffic, and it can also be easily blocked by firewalls.
Option D (nmap "sQ "O <system> -P0) uses the idle scan technique, which relies on finding an idle system on the network that is trusted by the target system and can be used to spoof packets to the target. This technique is complex and requires specific network conditions to work correctly, and it is not guaranteed to be stealthy or reliable.
Option C (nmap "sS "O <system> -P0) uses the TCP SYN scan technique, which sends packets with the SYN flag set and expects to receive a SYN/ACK response if the port is open or a RST response if the port is closed. This technique is the most stealthy of the four options, as it generates the least amount of traffic and can be difficult to detect. It is also very effective in identifying open ports and services on the target system, especially if combined with other Nmap options like -sV for service version detection.
