Question 90 of 270 from exam CAS-003: CompTIA CASP+
Question
An information security officer is responsible for one secure network and one office network.
Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks.
To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data:
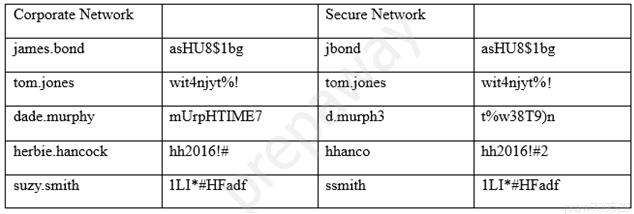
Which of the following tools was used to gather this information from the hashed values in the file?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.D.
