Question 225 of 270 from exam CAS-003: CompTIA CASP+
Question
While investigating suspicious activity on a server, a security administrator runs the following report:
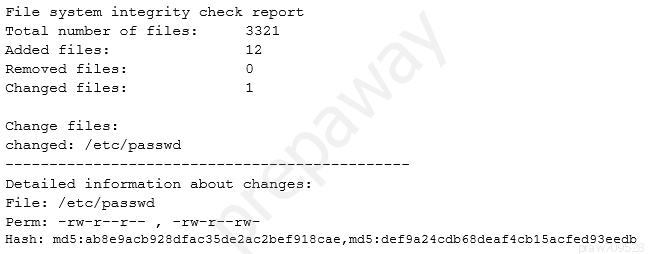
In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report.
Which of the following BEST describe this scenario? (Choose two.)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.AB.