Question 238 of 270 from exam CAS-003: CompTIA CASP+
Question
A security engineer successfully exploits an application during a penetration test.
As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application.
Given the information below from the screenshot.
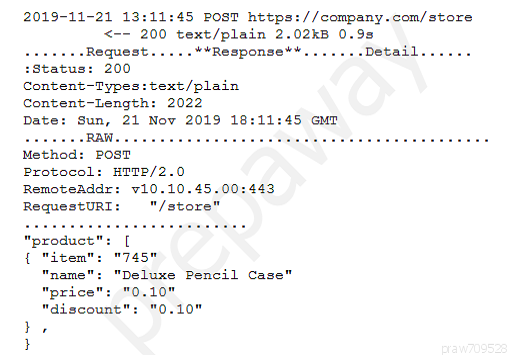
Which of the following tools was MOST likely used to exploit the application?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.B.
