Question 72 of 270 from exam CAS-003: CompTIA CASP+
Question
A company wants to extend its help desk availability beyond business hours.
The Chief Information Officer (CIO) decides to augment the help desk with a third- party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance.
The security administrator implements the following firewall change:
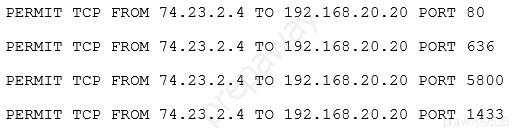
The administrator provides the appropriate path and credentials to the third-party company.
Which of the following technologies is MOST likely being used to provide access to the third company?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.D.