Question 17 of 44 from exam CAS-004: CompTIA CASP+
Question
A security engineer has been asked to close all non-secure connections from the corporate network.
The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS.
The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead.
The network comprises three VLANs:

The security engineer looks at the UTM firewall rules and finds the following:
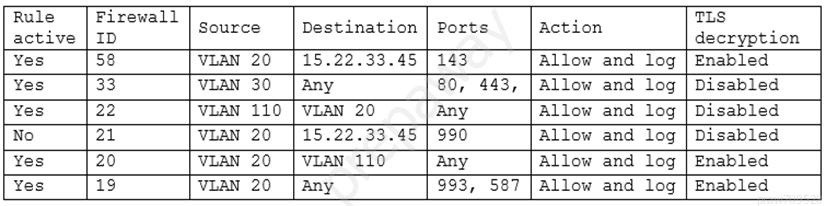
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.C.
