Question 34 of 44 from exam CAS-004: CompTIA CASP+
Question
Device event logs sources from MDM software as follows:
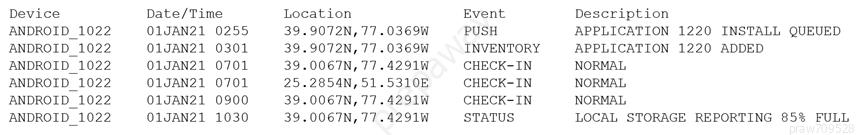
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.A.
