Question 141 of 160 from exam CS0-002: CompTIA CySA+
Question
An analyst is reviewing the following code output of a vulnerability scan:
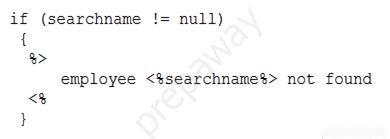
Which of the following types of vulnerabilities does this MOST likely represent?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.C.
