Question 22 of 160 from exam CS0-002: CompTIA CySA+
Question
A security analyst is reviewing the logs from an internal chat server.
The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity.
Below is a snippet of the log:
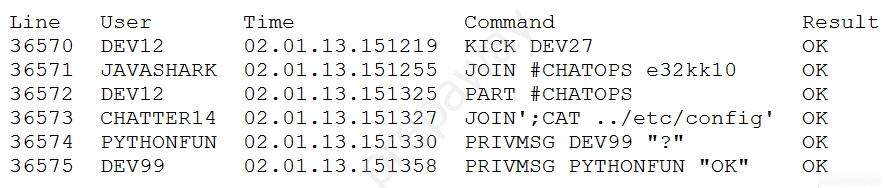
Which of the following commands would work BEST to achieve the desired result?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.D.
