Question 29 of 160 from exam CS0-002: CompTIA CySA+
Question
A security analyst is evaluating two vulnerability management tools for possible use in an organization.
The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
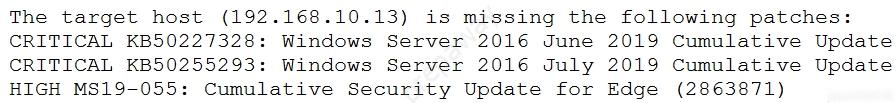
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.AF.