Question 64 of 160 from exam CS0-002: CompTIA CySA+
Question
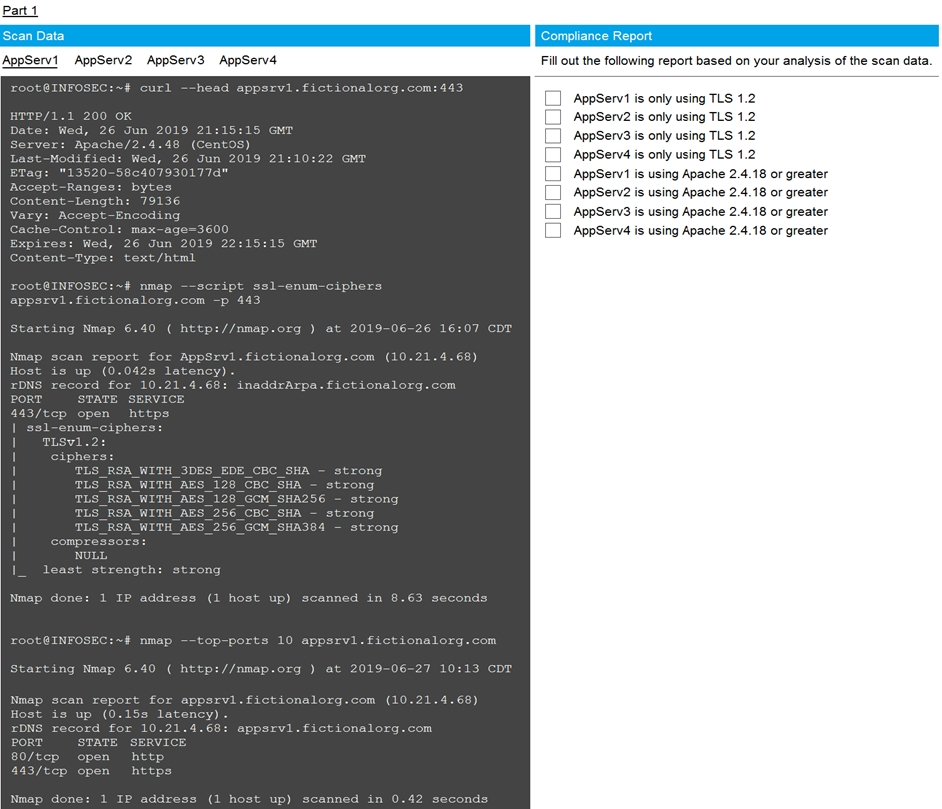
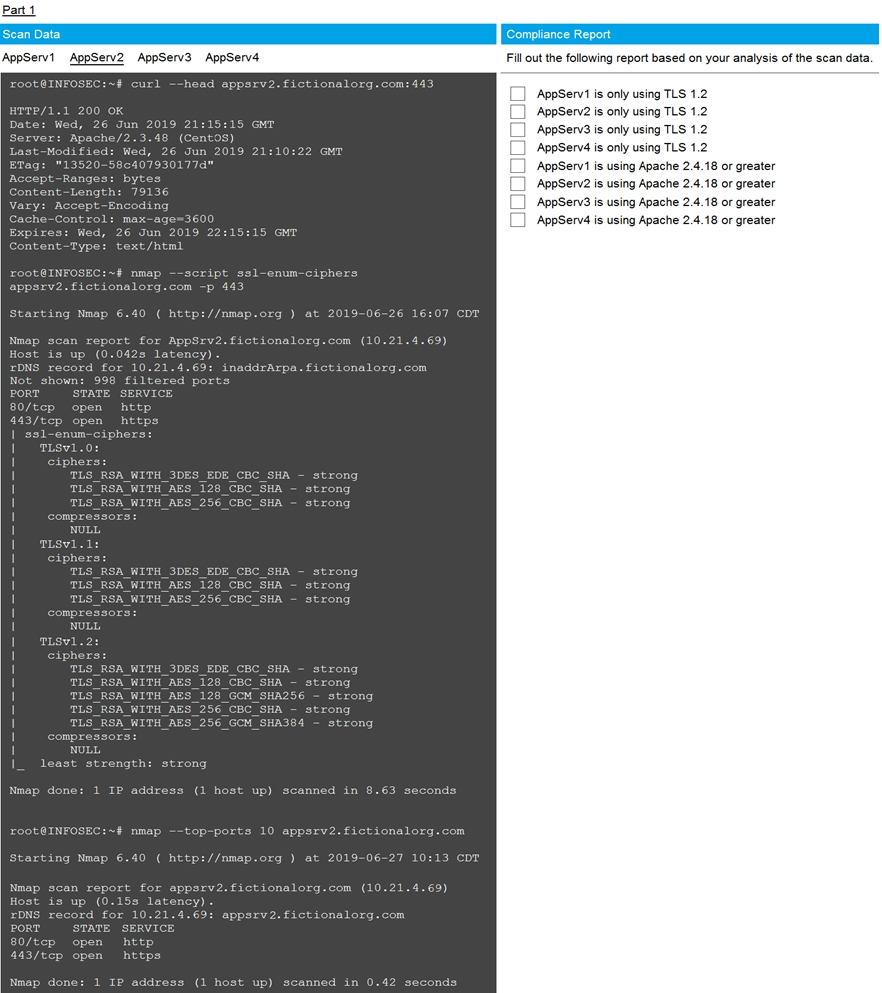
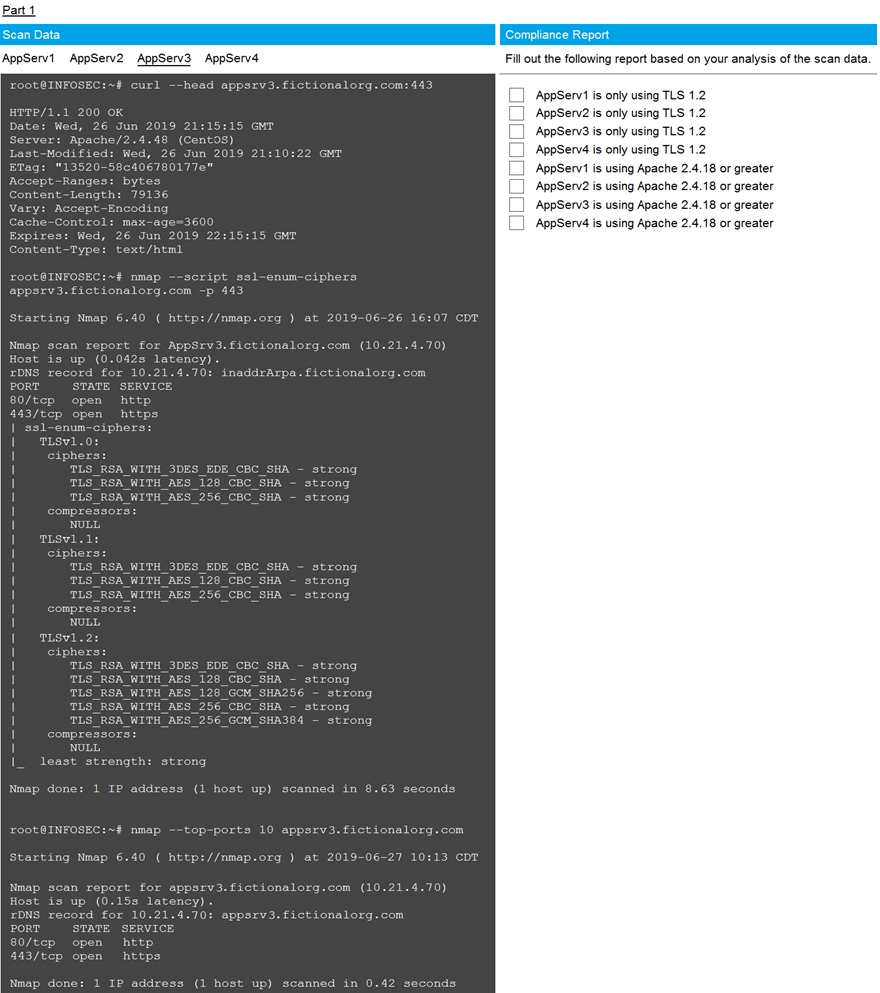
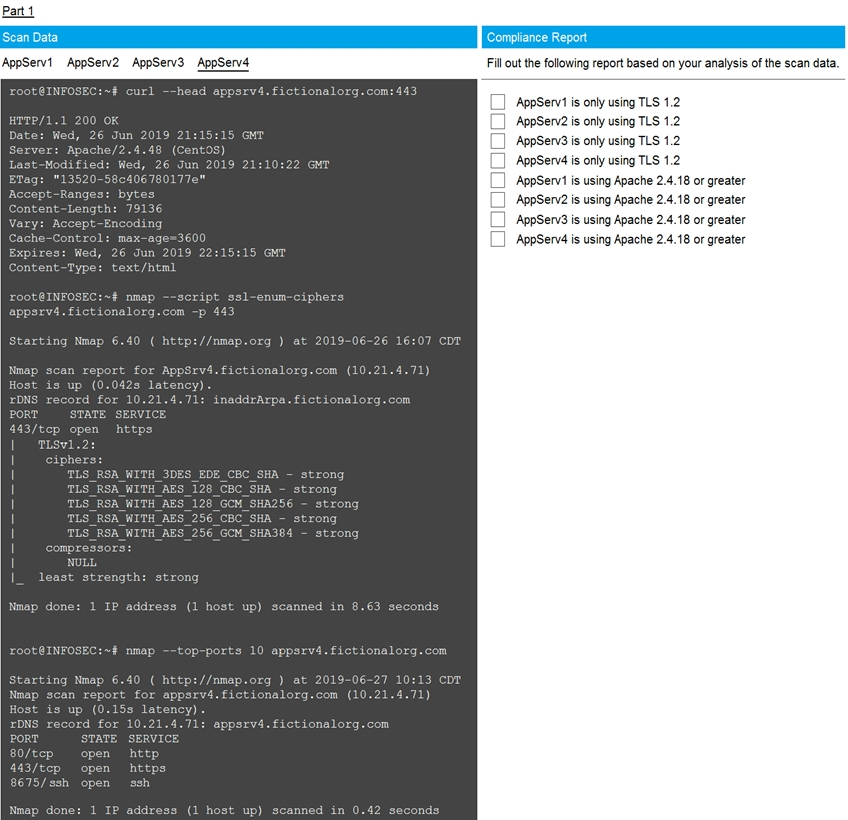
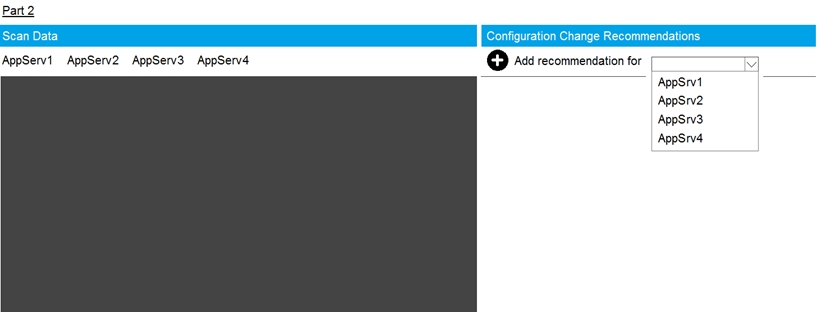
SIMULATION - You are a cybersecurity analyst tasked with interpreting scan data from Company A's servers.
You must verify the requirements are being met for all of the servers and recommend changes if you find they are not.
The company's hardening guidelines indicate the following: TLS 1.2 is the only version of TLS running.
Apache 2.4.18 or greater should be used.
Only default ports should be used.
INSTRUCTIONS - Using the supplied data, record the status of compliance with the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2
Make recommendations for issues based ONLY on the hardening guidelines provided.
Explanations
Part 1 Answer:
Check on the following: AppServ1 is only using TLS.1.2 - AppServ4 is only using TLS.1.2 - AppServ1 is using Apache 2.4.18 or greater AppServ3 is using Apache 2.4.18 or greater AppServ4 is using Apache 2.4.18 or greater Part 2 answer: Recommendation: Recommendation is to disable TLS v1.1 on AppServ2 and AppServ3.Also upgrade AppServ2 Apache to version 2.4.48 from its current version of 2.3.48
