Question 74 of 160 from exam CS0-002: CompTIA CySA+
Question
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident.
The analyst determines backups were not performed during this time and reviews the following:
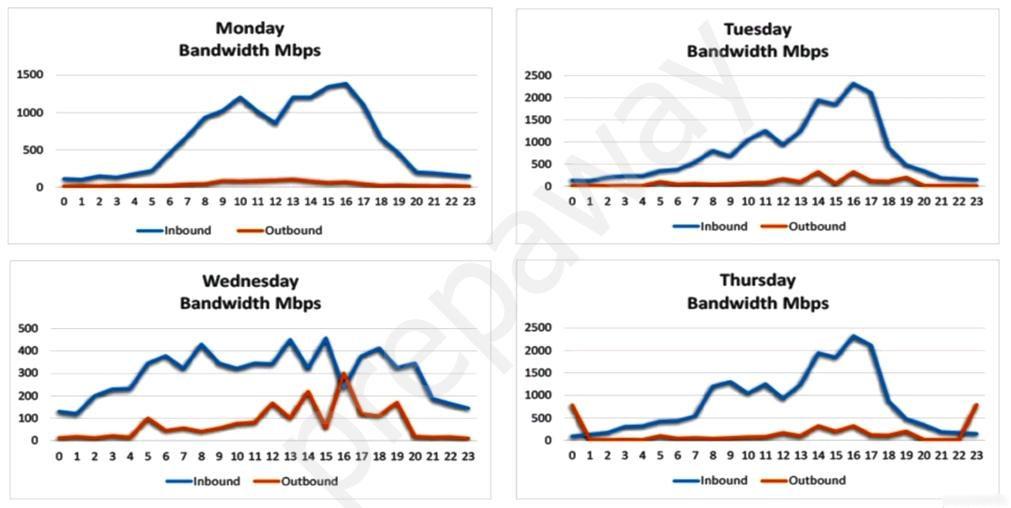
Which of the following should the analyst review to find out how the data was exfiltrated?
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D.C.