Question 12 of 52 from exam PT0-001: CompTIA PenTest+
Question
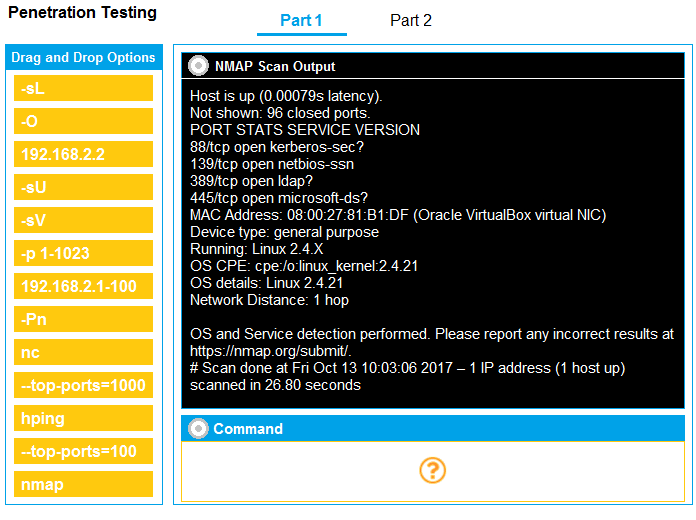
SIMULATION - You are a penetration tester running port scans on a server.
INSTRUCTIONS - Part 1: Given the output, construct the command that was used to generate this output from the available options.
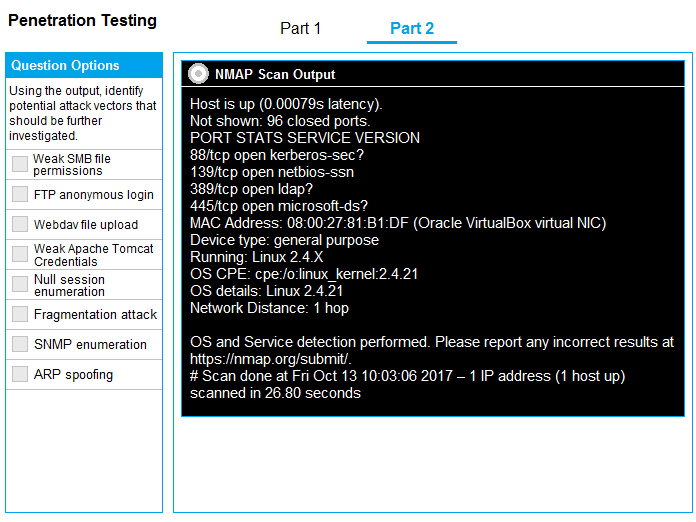
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Explanations
See explanation below.
Part 1 - nmap 192.168.2.2 -sV -O Part 2- Weak SMB file permissions.