Question 9 of 52 from exam PT0-001: CompTIA PenTest+
Question
A penetration tester recently completed a review of the security of a core network device within a corporate environment.
The key findings are as follows: * The following request was intercepted going to the network device: GET /login HTTP/1.1 - Host: 10.50.100.16 - User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 - Connection: keep-alive - Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk * Network management interfaces are available on the production network.
* An Nmap scan returned the following:
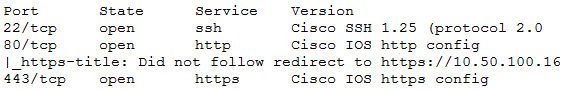
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.CE.