Connectivity Solution between On-Premises Infrastructure and Amazon VPC
Question
You are designing a connectivity solution between on-premises infrastructure and Amazon VPC.
Your servers on-premises will be communicating with your VPC instances.
You will be establishing IPSec tunnels over the internet.
You will be using Virtual Private Gateways and terminating the IPsec tunnels on AWS-supported customer gateways.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E. F.Answer - C, D, E and F.
IPSec is designed to provide authentication, integrity, and confidentiality of the data that is being transmitted.
IPSec operates at the network layer of the OSI model.
Hence, it only protects the data that is in transit over the internet.
For the full security of the data transmission, it is essential that both the sender and receiver need to be IPSec-aware.
See the diagram of this scenario:
Option A is incorrect because (a) IPSec operates at the network layer of the OSI model.
Hence, it only protects the data that is in transit ( encryption of data in transit ONLY) over the internet, and (b) both the source and the destination (client and server) may not be IPSec aware.
Option B is incorrect because the identity authentication of the origin of the data has to be done at the application layer, not the network layer.
Option C is CORRECT because the data that is transiting via the IPSec tunnel is encrypted.
Option D is CORRECT because IPSec protects the data in transit over the internet (fundamental responsibility of IPSec tunnel).
Option E is CORRECT because, in this scenario, it is a pre-requisite to have the Peer identity authentication between VP gateway and customer gateway for implementing an IPsec VPN tunnel.
The IPSec tunnel is established between the VP Gateway (VPG) and Customer Gateway (CGW) whose identity gets authenticated during the IPSec tunnel setup.
Since it is a pre-requisite even for establishing this connection we cannot term that as an objective that we have achieved via IPSec implementation.
Option F is CORRECT because - as mentioned earlier - the integrity of the data that is transiting via the IPSec tunnel is always preserved (fundamental responsibility of IPSec tunnel).
For more information on IPSec tunnel, please refer to.
http://techgenix.com/securing_data_in_transit_with_ipsec/The below link provides an article on the general working of an IPSec tunnel which outlines the advantages of an IPSec tunnel which includes:
http://www.firewall.cx/networking-topics/protocols/870-ipsec-modes.html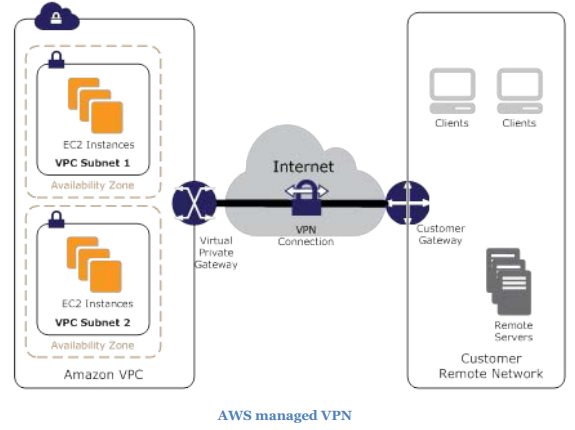
The scenario described involves establishing IPSec tunnels over the internet between on-premises infrastructure and Amazon VPC. The solution requires a secure connectivity solution that provides protection of data in transit over the internet and data encryption across the internet.
Virtual Private Gateways (VPGs) are the Amazon VPC side of a VPN connection. A VPG is a virtual router that is used to establish a secure IPsec tunnel between the on-premises network and Amazon VPC. AWS-supported customer gateways are the physical devices that terminate the IPsec tunnels on the on-premises network side.
Answer options A, D, and F are correct because they all relate to the protection of data in transit over the internet. IPSec provides end-to-end protection of data, including data encryption and data integrity protection. This ensures that data transmitted between on-premises infrastructure and Amazon VPC is protected from interception and tampering.
Answer option B is not required in this scenario as there is no mention of end-to-end identity authentication being required.
Answer option E is incorrect because peer identity authentication between Virtual Private Gateway and customer gateway is a requirement for establishing the VPN connection, not for the implementation of the solution.
