AWS Certified DevOps Engineer - Professional | DOP-C01 Exam Answer
Question
Which of the following will you need to consider so you can set up a solution that incorporates a single sign-on from your corporate AD or LDAP directory and restricts access for each user to a designated user folder in a bucket? Choose 3 answers from the options below.
Answers
Explanations
Click on the arrows to vote for the correct answer
A. B. C. D. E.Answer - A, B and D.
The below diagram showcases how authentication is carried out when having an identity broker.
This is an example of a SAML connection, but the same concept holds true for getting access to an AWS resource.
For more information on federated access, please visit the below link:
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_common-scenarios_federated-users.html https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-idp_saml.html?icmpid=docs_iam_console https://aws.amazon.com/blogs/security/writing-iam-policies-grant-access-to-user-specific-folders-in-an-amazon-s3-bucket/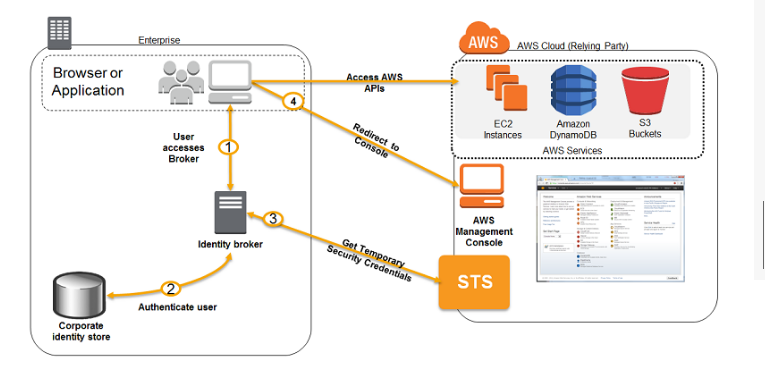
To set up a solution that incorporates a single sign-on (SSO) from your corporate AD or LDAP directory and restricts access for each user to a designated user folder in a bucket, you will need to consider the following three options:
A. Setting up a federation proxy or identity provider: A federation proxy or identity provider is used to establish trust between your corporate directory and AWS, allowing users to use their existing credentials to access AWS resources. You can set up a federation proxy or identity provider to allow users to authenticate with their corporate credentials and then obtain temporary security credentials to access the AWS resources. This option provides a single sign-on (SSO) experience to users.
B. Using AWS Security Token Service (STS) to generate temporary tokens: AWS Security Token Service (STS) allows you to grant users temporary access to AWS resources. With STS, you can generate temporary security credentials that provide restricted access to AWS resources. By using temporary credentials, you can reduce the risk of long-term access keys being compromised. You can use STS in combination with a federation proxy or identity provider to generate temporary credentials for users authenticated with their corporate credentials.
D. Configuring IAM role: An IAM role is an AWS identity that has specific permissions to access AWS resources. You can create an IAM role with permissions that allow users to access only their designated user folder in the bucket. By using IAM roles, you can easily manage permissions and access for multiple users.
Option C, tagging each folder in the bucket, is not necessary to achieve the desired outcome. Tags are used to categorize resources and can be used to track cost and usage. However, they do not provide access control.
Option E, setting up a matching IAM user for every user in your corporate directory that needs access to a folder in the bucket, is not recommended as it can lead to high management overheads. Instead, using a federation proxy or identity provider and temporary security credentials or IAM roles can provide a more efficient and secure solution.
In summary, to set up a solution that incorporates a single sign-on from your corporate AD or LDAP directory and restricts access for each user to a designated user folder in a bucket, you should consider using a federation proxy or identity provider, AWS Security Token Service (STS) to generate temporary tokens, and configuring IAM roles with specific permissions for accessing the designated user folder.
